In the 21st century ‘penetration’ has become like a common phrase to those who are constantly engaged in the world of ICT. Although penetration is not legally permitted, sometimes you cannot penetrate some anti-peace or anti-social people’s sites to have an overview of their destructive activities and take control of the sites to protect your society or country as a whole.
As the issue is becoming more important day by day, we are taking it seriously and taking the initiative to help you. Thus, in this article, we have listed some of the best Penetration Testing Tools that you can use with Kali Linux or any other Linux system for a great purpose.
Best Penetration Testing Tools for Linux
Here is a complete list of Penetration Testing Tools to be used with Linux. Each of the Penetration Testing Tools contains only precise information with which you can keep yourself updated on the world of technology.
1. Kismet Wireless
The specialists who basically work for the security of information or in the field of computer security must know Kismet along with the other penetration testing tools. They should also be aware of its capability.

Basically, it is computer software compatible with Linux, BSD, Microsoft Windows, and Mac OS X, which is used to identify and sniff the packets, and network traffic. It can also be used as a system of intrusion inhibition. Moreover, it is important for you to be aware that Kismet is an ‘open source security tool,’ which ensures that it is free for all.
2. Snort
Snort is one of the coolest penetration testing tools, and it is based on an open-source network. The software has the capability of performing packet logging on the networks of Internet Protocol and analysis of real-time traffic. It can also accomplish the searching and matching of content and analysis of protocol.

Moreover, you can use the software for detecting attacks or probes comprising stealth port scans, operating system fingerprinting efforts, server message block probes, overflow of the buffer, and semantic URL attacks.
3. Wireshark
Wireshark is fundamentally an analyzer of protocol or network, which you can get for free at its official website. The software is utilized to study the configuration of various network protocols. It owns the capability of demonstrating encapsulation.

You can operate the analyzer on Linux, Microsoft Windows, and Unix. Besides, the software can capture the packets engaging the pcap and the toolkit of GTK+ widget. However, Wireshark or other terminal-based software versions such as Tshark that are free are released under GNU.
4. Nessus
Nessus, which is a branded susceptibility scanner and has been advanced by ‘Tenable Network Security,’ holds a significant place among the penetration testing tools. You can use it for free only if you use it for personal use in a non-enterprise setting. However, it allows you to scan for numerous kinds of vulnerabilities.

The scan includes planning for PCI DSS audits, allowing a distant hacker to have access or control of a pack of sensitive data on a specific system, renunciations of service against the IP/TCP stack by utilizing deformed packets, default passwords, and misconfiguration. Additionally, the software can call a peripheral tool, known as ‘Hydra,’ to launch a dictionary attack.
5. Nmap
Nmap provides you with many features for examining the computer network, including the detection of operating systems and services and the discovery of hosts. The features also include the detection of OS and version, the discovery of the host, scanning of port, and scriptable communication with the target.

The software can offer additional information on the targets, comprising types of devices, MAC addresses, and the names of reverse DNS. The usual uses of Nmap are detecting and exploiting susceptibilities in a particular network, recognizing open ports in planning for inspection, reviewing the safety of a network by the identification of new servers, and many more.
6. Netcat
Netcat is a program expert in data reading and writing both in the UDP and TCP network links. The individuals who are basically liable for the security of both the system and network must know Netcat’s capabilities in detail. The list of the software’s features comprises port scanning, listening, and transferring files. You can also use it as a backdoor.

However, the unique netcat’s features many things including the capability of using a local source port and using the source address of a locally formed network, and it can even understand the arguments of the command line from any standard input.
7. Metasploit Framework

The ‘Metasploit Framework’ is a modular platform for penetration testing, which is essentially Ruby-based and allows you to compose, check, and perform exploit code. The software has a collection of tools with which you can examine security weaknesses, count networks, implement attacks, and avoid exposure.
In simple words, this software is a set of usually utilized tools that offer you an entire atmosphere for the testing of penetration and development of exploitation.
8. John the Ripper
‘John the Ripper’ is considered one of the fastest password crackers, which you can now get for numerous flavors of Windows, Unix, BeOS, OpenVMS, and DOS.

The initial motive of this cracker is to sense feeble Unix passwords. The software is exceptional to the older crackers as it usually doesn’t perform tasks using a ‘crypt(3)-style routine.’ Instead, the software owns extremely boosted modules for dissimilar processor architectures and hash types.
9. THC Hydra

THC Hydra is principally a parallelized logging cracker that backs much code of behavior to attack. The cracker is relatively quicker and more flexible than the other penetration testing tools, allowing you to add new modules easily. The tool helps security consultants and researchers to see how easily anyone can have unauthorized authority over their systems.
10. Aircrack-ng
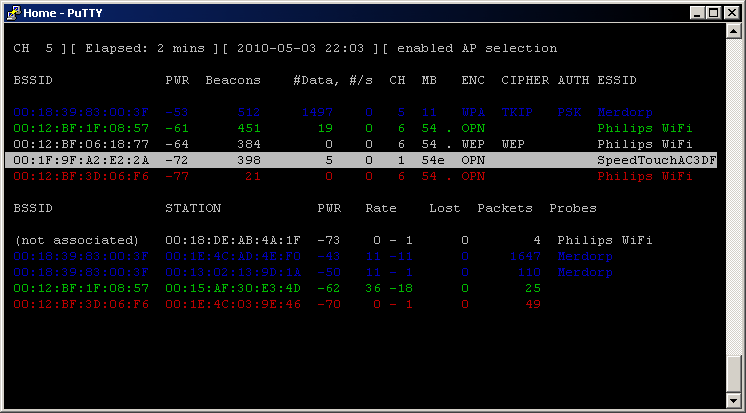
Aircrack-ng is a suite of network software that consists of a packet sniffer, a sensor, an investigation instrument for 802.11 wireless LANs, and a WPA/WPA2-PSK and WEP cracker.
The cracker can even work with an interface controller of a wireless network in which 802.11g traffic and sniff 802.11a, 802.11b, and raw observing mode are supported by its driver. You can operate the program using Windows, Linux, OpenBSD, FreeBSD, and OS X.
11. Nikto
Nikto is a scanner of a web server with an Open Source (GPL) facility. It can perform widespread investigations against web servers aimed at many items. The list of the items includes over 6700 possibly risky programs/files, investigations for non-operational versions of more than1250 servers, and type-specific difficulties on more than 270 servers.

Besides, the software inquiries for the items of server configuration like the attendance of numerous directory files, options for HTTP server, and attempts to detect the setup software and web servers. Moreover, it often scans plugins and items for an update.
12. Burp Suite Scanner
Burp, also called Burp Suite, is principally a graphical instrument appropriate for testing the security of Web applications. Java language has been used to write this tool, and ‘PortSwigger Web Security’ has developed it comprehensively.

This software was developed basically to provide you with a complete solution for checking the security of web applications. Besides having elementary functionality like an intruder scanner and proxy server, it also has more radical options like a sequencer, a spider, an extender, a repeater, a comparer, and a decoder.
13. Maltego

Maltego, advanced by Paterva, is exclusive software that is used widely for open source forensics and intelligence. It permits you to create custom entities, letting it signify any kind of information besides the elementary entity types that are part of this software.
Read Also: Most Comprehensive List of Linux Monitoring Tools For SysAdmin
The application basically focuses on the analysis of the associations with online services such as Facebook and Twitter and also the real-world associations between groups, people, domains, Web pages, networks, and internet infrastructure.

Among the data sources of Maltego, there are whois and DNS records, search engines, many APIs and metadata, and online social networks. However, the software is mostly used by private detectives and security investigators.
14. Fern Wifi Cracker

It is software that can evaluate the security of Wireless and attack software programs formed using the Python Qt GUI library and the Python Programming Language. The software can crack and recuperate the keys of WEP/WPA/WPS and additionally can operate the attacks based on another network, either on Ethernet-centered networks or wireless.

Major features of the cracker are: cracking of WEP with Chop-Chop, Fragmentation, Caffe-Latte, ARP Request Replay Hirte; saving of key in databank on effective crack automatically; hijacking of a session; accessing point assault system automatically, and so on.
15. Wifite2

Wifite 2 is undoubtedly one of the excellent penetration testing tools for wifi auditing, which has been designed for use with pretesting circulations of Linux like Pentoo, Kali Linux, and BackBox and also with any Linux distributions in association with wireless drivers that are patched for inoculation.
Derv82, which is the developer of this application, has lately uncovered a new type of tool, which is planned completely for the newest Kali version.
16. Yersinia
Yersinia is a structure that is suitable for accomplishing the attacks of layer 2. The program is intended to take benefit of some vulnerabilities in different network protocols. It can pretend to be a compact framework for the analysis and testing of the installed systems and network.

Assaults of the following network protocols are executed in this specific release: the protocol of Cisco discovery, the protocol of VLAN trunking, the straddling tree protocol, the protocol of dynamic trunking, the protocol of hot reserve router, the protocol of dynamic host structure, the protocol of inter-switch link.
17. Hashcat – Advanced Password Recovery
Hashcat is the self-announced world’s quickest password retrieval tool. Until 2015, the application had a patented code base, which is now available free of cost. The versions that the software owns are accessible for Windows, Linux, and OS X.

The versions can also come in either GPU or CPU-based variants. Cisco PIX, Microsoft LM hashes, MD4, SHA-family, MySQL, Unix Crypt formats, and MD5 are some of the examples of ‘Hashcat’ adopted hashing algorithms.
The application has come onto the front page of news several times because of its creator’s discovery of faults and optimizations. These were subjugated in the following hashcat releases.
18. BeEF – The Browser Exploitation Framework
BeEF, which is the short form of ‘Browser Exploitation Framework,’ holds importance amid the dominant specialized penetration testing tools. The framework adopts revolutionary methods that offer the skilled penetration tester real attack vectors of the client side.
This security framework is quite exceptional to other types of such frameworks in the sense that it concentrates on leveraging the weaknesses of any browser to evaluate a target’s safety posture.
Recommended Post: 15 Most Secure Linux Distros for Privacy and Security Concern Users
The project has been advanced only for legal investigation and penetration examination. Also, it has many modules for a command that engages the simple yet powerful API of this program. The API is considered the core of this framework’s efficiency as it summarizes difficulty and simplifies the rapid progress of the custom modules.
19. GNU MAC Changer

This is a useful tool that helps you to view and change the MAC addresses of different networking tools. You can also set new addresses randomly or explicitly. The addresses comprise the MAC addresses of either the similar or other sellers’ hardware. More usually, these may include MAC addresses of the same type of hardware.
20. PixieWPS Brute Force Offline Tool

Pixiewps is mostly utilized for off-line brute compelling of the WPS pins when at the same time exploiting the non-existing or low entropy of certain wireless entree points that are also called the attack of pixie dust. Dominique Bongard at first discovered it.
21. BBQSQL – SQL Injection Exploitation Tool
BBQSQL is a framework that functions following blind SQL injection. It is inscribed in Python. The program is very convenient while attacking complicated SQL injection susceptibilities.
Besides, it is a half-automated tool that allows a fair bit of personalization for those trying to activate findings of SQL injection. Furthermore, the tool has been made to act as database agnostic, which is exceptionally versatile. It has an intuitive UI as well that makes setting up attacks stress-free.
22. cisco-torch
Cisco Torch, bulk exploitation, scanning, and fingerprinting tools were inscribed when the work on the subsequent version of the “Hacking Exposed Cisco Networks” was going on as the programs found in the market were unable to bring an epoch-making solution.

The core quality that makes the tool dissimilar to the other identical types of penetration testing tools is the wide usage of forking to introduce numerous scanning procedures for furthermost scanning competence. Besides, the program utilizes some approaches of application coating fingerprinting instantaneously, if required.
23. copy-router-config
The ‘copy-router-config’ is a tool whose menu element is a convenient tiny Perl script that is placed together. This menu item is placed inside the ‘Backtrack’ menu, and when you press the item, this menu item introduces a station window in the ‘’/pentest/cisco/copy-router-config’’ manual so that you can get a straight entrée to the ‘35 line Perl script’, that serves a particular purpose only.
The motive is to reproduce a complete router structure file from any Cisco device only if your router has an ‘RW community string.’
24. DBPwAudit
DBPwAudit is essentially a Java instrument that lets you perform online inspections of the password’ quality for some database engines. The design of this application allows you to add supplementary database drivers to the JDBC manual by just reproducing the fresh JDBC drivers.

The configuration of the program is accomplished in two different files: the rules.conf is employed to instruct the application regarding its handling of the fault messages received from scanning while the aliases.conf file is employed to map the drivers to pseudonyms.
Recommended Post: Best 20 Linux Window Managers: A Comprehensive List for Linux Users
However, the tool is verified and flexibly works with MySQL, Oracle 8/9/10/11, Microsoft SQL Server, and IBM DB2 Universal Database 2000/2005. The program is pre-constituted for the mentioned drivers, though it doesn’t ship with these because of licensing issues.
25. HexorBase
HexorBase is a databank program that is planned to run and check numerous database servers instantaneously from a central place. The application is skilled in executing brute force assaults and SQL inquiries against mutual database servers, including PostgreSQL, MySQL, Microsoft SQL Server, SQLite, and Oracle.
It also permits the routing of the packet through substitutions or some time even through ‘’Metasploit pivoting antics’’ to interconnect with distantly unreachable servers that are concealed within the limited subnets.
Recommended Post: Linux Terminal Emulator: Top 15 Reviewed and Compared
This tool can work on Windows and Linux, which are operating the following: python-qscintilla2, python-pymssql, python-mysqldb, python-psycopg2, python-qt4, python, cx_Oracle.
26. Inguma – Penetration Testing Toolkit
This program is a strong penetration examining toolkit, which is completely written using Python. The application comprises modules for discovering hosts, gathering information regarding the fuzz targets, forcing the usernames and passwords, and potentially exploiting numerous products.

These all have made it one of the unconquerable penetration testing tools. Actually, it was primarily oriented to assault the systems related to Oracle, but you can also use it for all types of setups.
But, it is a matter of sorrow that at present the application cannot function with Win32. Again, the trouble with the Scapy library and RAW sockets does not function for Win32. But, if you are currently operating Win2k, you may have to face less difficulty.
27. ProxyChains
A proxy server refers to a devoted software or computer system being operated on such a computer that performs like an arbitrator between an end tool like a computer and an additional server that responds to any client’s service request.

Through the connection to the internet using proxies, the IP address of a client remains secret. Instead of showing the real IP address, the proxy server’s IP address is displayed. This is how a proxy provides a user with further confidentiality.
Recommended Post: Best Linux Task Manager: Top 12 Reviewed For Linux Nerds
However, the features of this fabulous ProxyChains are: you can use it with servers such as Sendmail and Squid; you can easily deal with any application of TCP client; you can mix it up with an entirely dissimilar proxy type on a list; it supports proxy servers of HTTP CONNECT, SOCKS4, and SOCKS5; the application also lacks any sort of chaining option technique.
28. WhatWeb
WhatWeb is another great tool that can identify any website. The purpose of the framework is to inform you about the features and functionality of a Website. The application identifies web tools comprising embedded devices, content management systems shortly known as CMS, web servers, blogging platforms, JavaScript libraries, and analytics/statistic packages.

It owns more than 1700 plugins, each of which is mechanized to spot something altered. Besides, it can identify SQL errors, version numbers, modules of a web framework, account IDs, email addresses, and so on.
Recommended Post: Top 15 Online Linux Terminal Emulators and Bash Editors
Some of the impressive features are the availability of numerous log formats such as ElasticSearch, SQL, RubyObject, Brief, Verbose, MongoDB, XML, MagicTree, and JSON; wheels the adjustment between dependability and stealth/speed; regulates the webpage redirection.
29. Dirbuster
This is considered one of the best penetration testing tools. It is essentially a multi-threaded Java program, which is intended to brute force the names of the files and manuals on the application/web servers. DirBuster makes attempts to discover the hidden applications and pages of a web server.

Whatever, this type of tool is frequently as simply worthy as the file and manual list they appear in. A completely dissimilar methodology was adopted to generate this. At last, this list was produced from scratch, by swarming the internet and gathering the files and manual, which are essentially utilized by the developers.
Recommended Post: Top 40 Best Linux Commands Cheat Sheet. Get It Free Now
The application offers a complete 9, unlike lists that make DirBuster tremendously operational at discovering concealed manuals and files. If it is insufficient, the program includes an option for performing an uncontaminated brute force that forces the unseen files and manual to show up.
30. Traceroute
Traceroute is an impressive helper that displays the route and measures the packets’ transit suspensions across an IP network. The traceroute keeps functioning until all of the delivered packets vanish over twice. When these are lost, the link is also lost, and the path can’t be assessed anymore.
31. HTTRACK

HTTRACK is a free and cool offline browser application that lets you download a worldwide website from the Internet to a native manual by constructing all of the manuals recursively, getting images, other files, and HTML from a specific server to a computer. Also, HTTrack updates a prevailing imitated site and continues the paused downloads. However, it is completely configurable and also owns a combined assistance system.
32. Openvas

OpenVAS is another mind-blowing program of tools and services that offers a wide-ranging and influential susceptibility scanning and weakness administration resolution. It is an effective susceptibility managing resolution under the ‘’Greenbone Networks,’’ from which the improvements have been funded to the ‘’Open Source community’’ since 2009.
The Last Words
So, this is how the above-discussed Penetration Testing tools can help you with penetration with Linux. We hope you have already gone through the entire writing and are puzzled by the tools’ excellence.
Recommended Post: 27 Best Linux Tutorial Books That You Need To Download Now
If our assumption is not wrong, then leave an encouraging comment for us so that we can present you with more fabulous writing subsequently. Furthermore, kindly share the article with your friends and relatives to help them become versed in operating penetration testing tools, which is another source of inspiration.


