The netstat (network statistics) utility in Linux provides information related to network connections. You can use various netstat commands to display active network connections, interface data, routing tables, and so on.
These are essential information for network admins and infosec professionals. That’s why we have prepared this guide with a wide selection of useful netstat examples.
After completing this guide, you will be able to inspect all the network-related information for your Linux machine. We also encourage readers to try these examples on their own machine to obtain a more hands-on experience.
Netstat Command Examples for Network Admins
The information provided by netstat makes it easy to locate problems in network connections. This is why netstat is the go-to utility for troubleshooting network connections for many sysadmins. Continue reading to find out how to use the netstat command best.
1. Display All Active Sockets
Sockets are structures that act as endpoints when sending or receiving network requests. When used without any arguments, netstat displays a list of all the open sockets in your machine.
$ netstat
By default, this command shows the active sockets for all network families. As you might notice, it prints out a lot of additional information under the label “Unix Domain Sockets“. These are the data communication endpoints for the currently running processes on your machine.
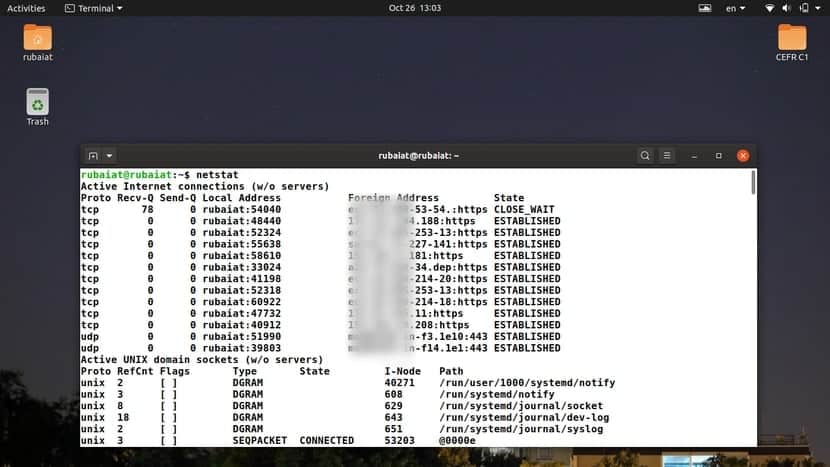
2. Display All Listening and Non-Listening Sockets
You can use the -a option of netstat to print out a list of all listening and non-listening sockets. Run the following command and check the output to see how this command works.
$ netstat -a $ netstat --all
The –all option works the same as -a. The output should show all the sockets, both active and inactive. The rows represent the sockets, and the column dictates their values. Users can view the socket protocol, data sent/received, addresses, and corresponding states.
3. Display TCP Connections
The TCP or Transmission Control Protocol is the most used internet protocol. You can use the following netstat command to display the active TCP connections only.
$ netstat -t $ netstat --tcp
You can also use the long-form –tcp instead of -t. Use the below command to view a list of all listening and established TCP network connections.
$ netstat -at $ netstat -all --tcp
4. Display UDP Connections
UDP, or User Datagram Protocol, is another major network protocol used by our systems. You can use the netstat utility to display a list of established and listening sockets for UDP connections.
$ netstat -u $ netstat --udp
This example prints all established UDP connections. If you want to view all established as well as listening connections, use the below command instead.
$ netstat -au $ netstat --all --udp
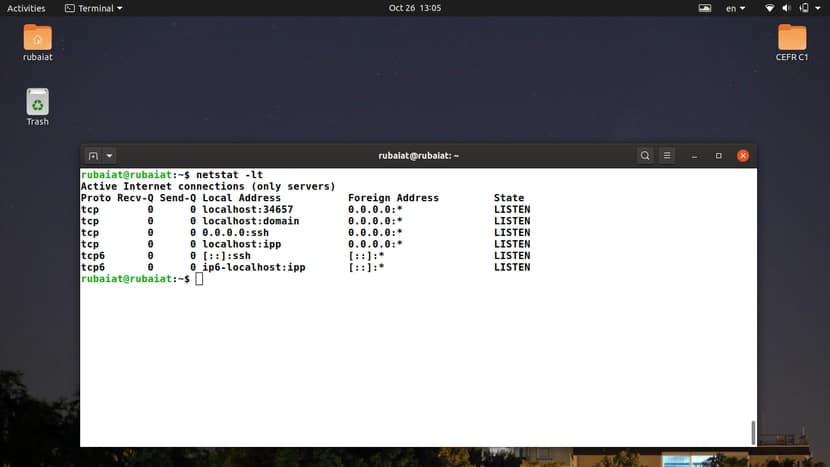
5. Display All Listening TCP Connections
You can display a list of all listening TCP connections using the -l and -t flags of the Netstat program. Check out the below command to see how that happens.
$ netstat -lt
It will display all TCP connections that are actively listening for incoming network requests. The output should contain information about both TCP and TCP6 protocols. You can also use the long-form syntax when using this command in Linux shell scripts.
$ netstat --listen --tcp
6. Display All Listening UDP Connections
Users can take the same approach shown in the above command to display listening UDP connections. Open your favorite Linux terminal emulator and run the below command to do so.
$ netstat -lu
As with the earlier command, it will show connections for the UDP and UDP6 protocols. The below example illustrates the long form.
$ netstat --listen --udp
7. Display All Listening UDP-Lite Connections
UDP-Lite is a connection-less protocol based on the UDP protocol. It allows systems to receive a potentially damaged network packet. You can display the listening connections for this protocol by using the following simple command.
$ netstat -lU
The -U option of Netstat allows admins to specify the udplite protocol. You may also use –udplite as the long-form for this option.
$ netstat --udplite
8. Display Listening Unix Connections
We have already discussed how Linux systems use the Unix domain socket for inter-process communication(IPC). You can print out a list of all listening Unix connections for your machine using the following netstat command.
$ netstat -lx
The -x option specifies the Unix domain sockets. You may use the abbreviated form –unix instead of -x. This is useful for documenting shell scripts.
$ netstat --unix
9. Display Protocol Statistics
The netstat utility offers excellent support for protocol statistics. Users can view a wide range of information from the statistics data, such as the number of connections, packets, bad segments, etc. Check out the result for the next command to see how this works.
$ netstat -s $ netstat --statistics
By default, this command shows information about the TCP, UDP, ICMP, and IP protocols. Network admins can use this output to determine potential problems in network connections.
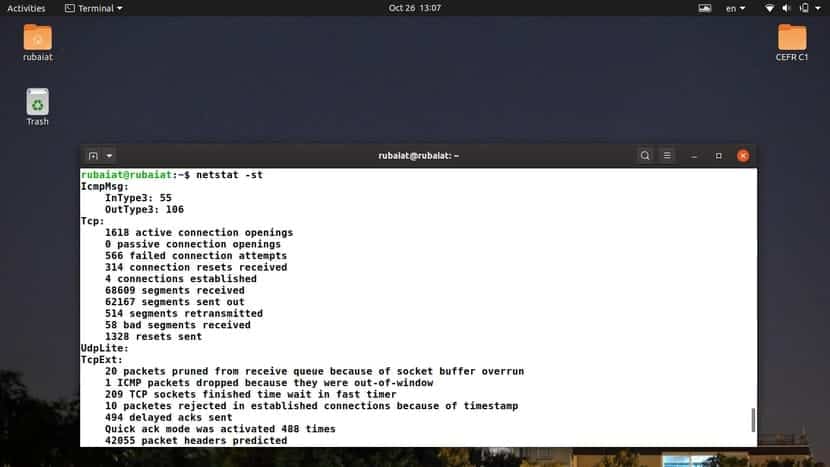
10. Display TCP Protocol Statistics
Users can also view connection statistics for a single protocol only. The following example displays the statistics data for only the TCP protocol.
$ netstat -st
We can easily combine the -s option with a protocol selector and find out statistics data about it. The example below prints the same output but uses the abbreviated syntax.
$ netstat --statistics --tcp
11. Display UDP Protocol Statistics
We can view the statistics data for the UDP protocol the same way we viewed TCP statistics. Replace the -t or –-tcp option with any of -u or –udp. Check out the next two examples to see how this works.
$ netstat -su $ netstat --statistics --udp
Note that you will also find the udplite statistics from these commands. However, if you specify udplite using the -U or –udplite option, there will be no UDP data on the resulting output.
12. Display Program Names
You can use the netstat utility to display which programs have initiated the network connections. This can be extremely useful when troubleshooting network issues. Check out the below command to see how it works.
$ netstat -pt
The output should contain established TCP connections and the programs that are responsible for those connections. You may also use the abbreviated form –program instead of -p, as illustrated in the below example.
$ netstat --program --tcp
13. Display Network Information in Continuous Mode
The -c or –continuous options of netstat allows it to display the specified information continuously. Check out the below commands to see how this works.
$ netstat -tc $ netstat --tcp --continuous
The default refresh interval is 1 second. However, users can override it by supplying an additional argument, as shown in the below examples.
$ netstat -tc 5 $ netstat --tcp --continuous 3
Contrary to many Linux terminal commands, the interval selector isn’t preceded by an equal sign for the abbreviated syntax.
14. Display the Routing Tables
The network utility can be used to display the routing tables defined by the Linux kernel. The output is similar to the one provided by the Linux IP command.
$ netstat -r
This command’s output shows information like the destination address, gateway, subnet mask, and network interface name. You may use the abbreviated syntax –route if you want to document this command’s use in your shell scripts.
$ netstat --route
15. Display Interface Statistics
Netstat can be used to print out the interface statistics for your Linux system. The following command prints out the available network interfaces and provides information about the transmitted and received packets, error rate, and MTU.
$ netstat -i $ netstat --interfaces
You can use either one of the options to view network interface information.
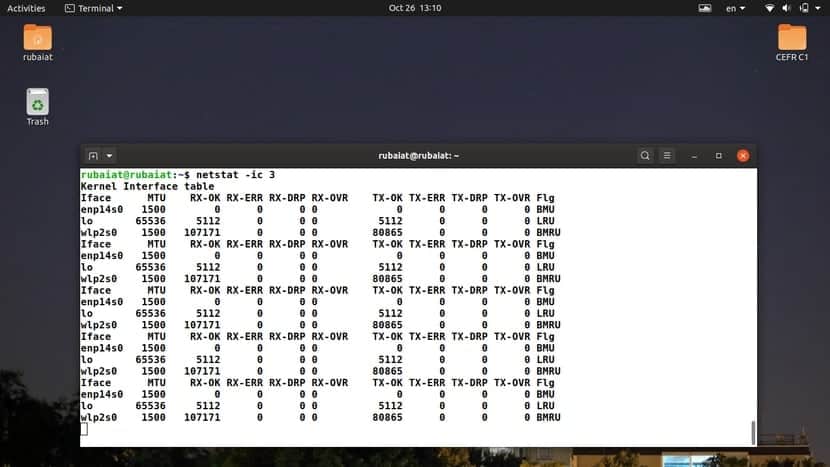
16. Display Interface Statistics in Real-Time
To view interface statistics in real-time, combine the -c or –continuous option with the interface option. The following examples will update the network interface statistics every 3 seconds.
$ netstat -ic 3 $ netstat --interfaces --continuous 3
You should notice changes under the transmitted(TX) and received(RX) fields. Replace the time interval with a number that suits your needs. Note that the interval is in seconds, not minutes.
17. Display Kernel Table for Interfaces
The following netstat command displays the interface table defined by the Linux kernel. This command is similar to the output provided by the Linux ifconfig command.
$ netstat -ie
The -e or –extend option forces netstat to print this interface table. The following example illustrates the same command using the abbreviated syntax.
$ netstat --interfaces --extend
18. Display IP Information
You can display the IPv4/IPv6 group memberships very easily by using the netstat utility. Check out the following simple example to see how this works.
$ netstat -g $ netstat --groups
So, the -g or –groups option of netstat can view the multicast group memberships.
19. Display Listening Programs
You can use the Netstat program to view which programs are actively listening for incoming network requests. This is very useful since you can determine which programs are responsible for certain network activities from this output.
$ netstat -ap | grep "http" $ netstat --all --program | grep "http"
We are simply printing all the listening programs and then filtering out the necessary listings by using grep. Check out our earlier guide on Linux grep commands to see how GREP filters piped data.
20. Display RAW Network Statistics
The following netstat example shows you how to use it to display raw network statistics. Copy the command and run it in your terminal emulator to view the output for your personal machine.
$ netstat -sw $ netstat --statistics --raw
The output should contain statistics data for raw network connections, including for IP, ICMP, and udplite.
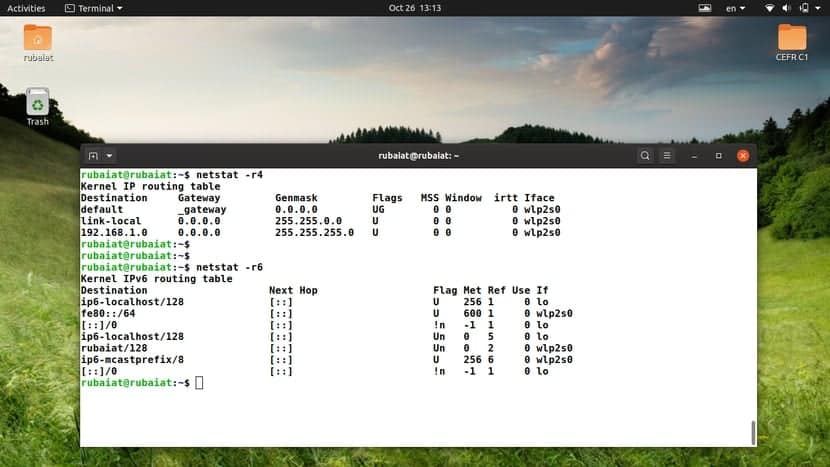
21. Display Information for IPv4 Routes
You can use the route sub-subcommand of netstat to view the IPv4 routes defined by the kernel. Check out the following example to learn how to do this.
$ netstat -r -4 $ netstat --route --inet
So, –inet is the abbreviated form for this option. You can also combine the options if you are using the short form.
$ netstat -r4
22. Display Information for IPv6 Routes
We can print the IPv6 routing information similarly to the above command. Use the -6 or –inet6 option along with the –route or -r flag. The following example illustrates this for readers.
$ netstat -r -6 $ netstat --route --inet6
Note that the output fields vary between IPv4 and IPv6. So, make sure to read the column labels. The below example combines the short forms of the IPv6 address family.
$ netstat -r6
23. Display Masquerade Connections
Masquerade connections allow one or more systems, without specified IPs, to connect to the internet using the addresses assigned by the Linux server. You can view a list of masquerade network connections and their statistics using the following netstat command in Linux.
$ netstat -M $ netstat --masquerade
When you run one of the above commands, netstat retrieves the required information by reading your Linux file system’s /proc/net/ip_masquerade file.
24. Display Network Timers
You can determine whether there are any timers for your network connections using the -o option of netstat. This can be helpful when you’re trying to troubleshoot outgoing network requests. Check out the following commands to see how this works.
$ netstat -t -o | more $ netstat --tcp --timers | more
The output should contain whether there are any timers present and if any, their type. Two slashes separate the three-timer fields. The first field is the countdown timer, and the second one is for tracking the number of retries. Finally, the last field tracks the number of keepalive probes that have been sent by the TCP stack.
25. Display IP Addresses Instead of FQDN
By default, netstat tries to resolve DNS when printing the network statistics. However, you can easily disable it and print the associated IP addresses instead of the FQDN(Fully Qualified Domain Name). This is useful for network monitoring and troubleshooting.
$ netstat --numeric-hosts --tcp --all
The –numeric-hosts option signals netstat to skip the DNS resolutions and print the numeric IP addresses instead. Check out our guide on Ubuntu DNS Servers to learn more about the domain name system.
26. Display Numerical Port Numbers
You can omit the symbolic port information from your netstat outputs by using the –numeric-ports option. This option forces netstat to print the numerical port numbers instead. Please check out the below example to see how it works.
$ netstat --numeric-ports --tcp --all
Compare the output with the previous example to locate the differences. You will find that this output contains exact port number representations. This is the number succeeding the host portion of your output, preceded by a colon.
27. Display the User ID for Network Connections
The following example demonstrates how to display the user ID for the user that owns the network connections. This can be done by using two options of the netstat command.
$ netstat --numeric-users --tcp -e
The -e option prints out the user’s name, and –numeric-users converts it into identification numbers. This is the UID(User Identification) set for each user by your Linux system.
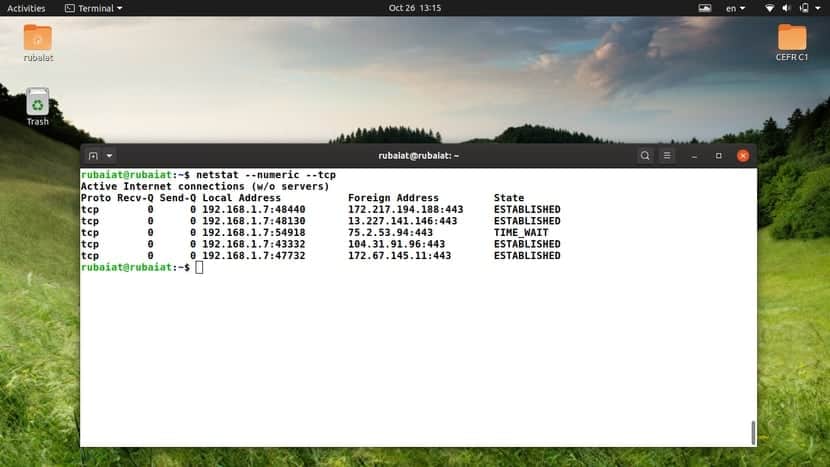
28. Display Numerical Equivalents for Hosts, Ports, and Users
You can combine the above three netstat commands using a single option. This will force netstat to print all hosts, ports, and user information using their numerical equivalent. Check out the following examples to see what we mean.
$ netstat -nt $ netstat --numeric --tcp
You can use either one of –numeric or -n for doing this. If you look at the output, you should see the IP addresses, port numbers, and UID information in numeric form.
29. Display Additional Information
The -e or –extend options of the netstat utility allow users to display extra information for their commands. These can lead to the discovery of hidden bugs. Check out the below example to see how it works.
$ netstat -tpe
This command combines the -t, -p, and -e options to print out the established TCP connections, the programs that own them, and some extra information. This extra information includes the user and inode information. Use the -e option twice to get more information.
$ netstat --tcp --program --extend --extend
30. Display the Kernel Routing Cache
The routing cache contains the routing entries that were used most recently. Since this is cached data, the information can be accessed very quickly. You can use the following command to print the route cache using netstat.
$ netstat -rC
By default, netstat retrieves the route information from the FTB. However, since systems usually use cached data before looking up the routing table, it can be useful to know what contents are stored there. There is no long form for this parameter.
31. Display Information for Multiple Protocols
Netstat allows users to print network information for a set of protocols using the -A or –protocol option. The following examples illustrate the usage of these options.
$ netstat -A inet,inet6 $ netstat --protocol=inet,inet6
Notice the difference between the usage of –protocol and -A. The supported address families for these options include inet, inet6, unix, ddp, bluetooth, etc.
32. Display SCTP Information
SCTP, or Stream Control Transmission Protocol, is a new and reliable method of data transfer. It offers the benefits of both the TCP protocol and UDP protocol. You can find out all listening to SCTP connections using the following simple commands.
$ netstat -lS $ netstat --listen --sctp
Remember not to use -s for this task. It will show network statistics instead. You can find out the detailed usage of SCTP using any of the netstat command examples listed below.
$ netstat -sS $ netstat --statistics --sctp
33. Display Bluetooth Information
The wireless data exchange standard Bluetooth utilizes several communication protocols. The Logical Link Control And Adaptation Protocol (L2CAP) and Radio Frequency Communication (RFCOMM) are two of its primary protocols used at the host level. You can display information about L2CAP using the following commands.
$ netstat -2 $ netstat --l2cap
Use the following commands to display information regarding the RFCOMM protocol.
$ netstat -f $ netstat --rfcomm
Note that many implementations of Netstat don’t offer out-of-the-box Bluetooth support. If you get the prompt “netstat: feature `AF BLUETOOTH’ not supported.“, then you will need to re-compile the net-tools utility from the source.
34. Display Symbolic Values for Hosts, Ports, and Users
The -N or –symbolic options of the netstat command allow us to print all information about hosts, ports, and users in symbolic form. Check out the following example to learn how it works.
$ netstat -atN $ netstat --all --tcp --symbolic
The output of these commands will contain a list of all the TCP networks, and the host, port, and users will be specified using their symbolic equivalent. It can be useful for admins who want verbose output rather than numerical ones.
35. Disable IP Address Truncation
You can use the -w or –wide options of the netstat utility to disable IP addresses’ truncation. This is not very useful on its own but offers a means of backward compatibility.
$ netstat -atw $ netstat --all --tcp --wide
If you are writing Linux shell scripts, use this option to make sure it doesn’t truncate the IP addresses on older machines.
36. Display Which Services are Listening on a Particular Port
If you are a white-hat hacker or infosec professional, you may want to view which are listening on a specific port. This can be done very easily by combining netstat with the grep command in Linux. Check out the following netstat example to learn how it can be done.
$ netstat -ltnp | grep ':22'
This command will print all programs that are listening to TCP port 22. This is the port number for SSH connections. Replace this number with the port number of your interest in the grep portion.
37. Display Non-Supported Address Families
As discussed already, netstat can work with a wide array of address families. However, not all of them are supported by every netstat implementation. For example, many netstat versions do not support the Bluetooth address family right out of the box. You can easily check the address families that are not supported by your netstat utility.
$ netstat --verbose | grep "no support for"
This command will print out all the unsupported address families for your machine. If you want to use any of them, you will need to fetch the source for net-tools and compile it with the full configuration support.
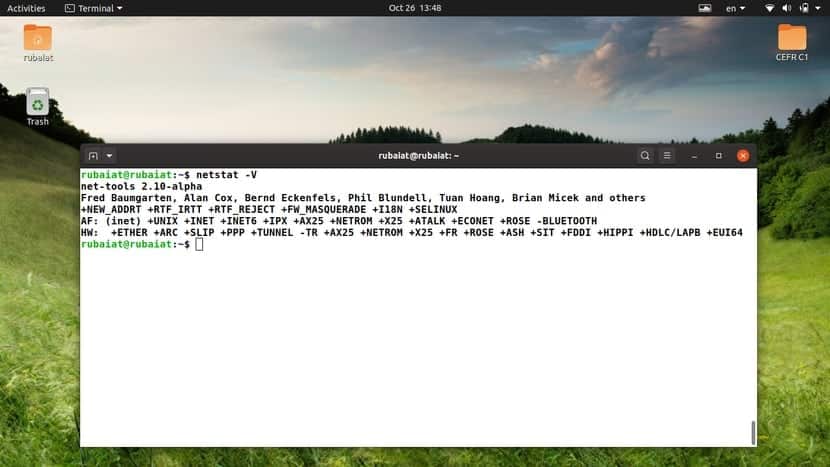
38. Display Version Information
You can print the version information for your netstat program using the -V or –version option. This will print some additional information alongside the version data.
$ netstat -V $ netstat --version
When you run one of the above commands, you will see a list of supported and unsupported address families. Note that the version data shown by this command represents the version of net-tools installed on your machine.
39. Display the Help Page
The help page of Netstat contains summarized information on all available options and their usage. It offers a convenient way of looking up the options. You can print this page by using one of the following netstat commands.
$ netstat -h $ netstat --help
If you are a network admin, you will find this section quite handy.
40. Display the Manual Page
The manual page of Linux terminal commands contains in-depth information about the command’s usage and available options. You should consult this page whenever you want to learn more about a specific program. The man page of netstat can be invoked using the below command.
$ man netstat
Check out this page if you want elaborate information on netstat and its output format.
Ending Thoughts
The netstat command is one of the most widely used terminal commands for sysadmins. However, it has become obsolete nowadays, and more advanced programs have emerged to take over.
The replacement for netstat, in general, is the ss program. The IP utility serves as the replacement for netstat -r, netstat -i, and netstat -g. Nevertheless, netstat remains quite relevant due to its widespread usage and availability on most Linux distributions.
We highly encourage our readers to use the newer alternatives. This coverage of the essential netstat commands can serve as a reference point for users who need to use netstat.