When it comes to establishing stable, secure networks, Linux is the first choice for a majority of us. This accounts for many things, including the massive array of networking tools and commands Linux provides.
You can find a seemingly infinite number of network utilities that will enable you to set up secure networks, monitor them for problems, troubleshoot effectively, and so on.
The list is, in fact, so extensive that most tutorials on the internet don’t even try to cover them. That’s why we’ve curated this well-thought-out guide on various Linux network commands.
Linux Network Commands for SysAdmins
We’ve tried to divide this entire guide into specific portions based on tools and their usage. You can use many of these commands in different scenarios. So their grouping isn’t strict per se – they are here to help you visualize.
Although this guide won’t cover every Linux network command, you can use this as a reference point whenever you get stuck with networking.
Linux Network Commands for Managing Network Interfaces
Configuring and managing network interfaces is essential for system admins and power users. This section will review some fundamental network commands available in Unix-like systems for this job.
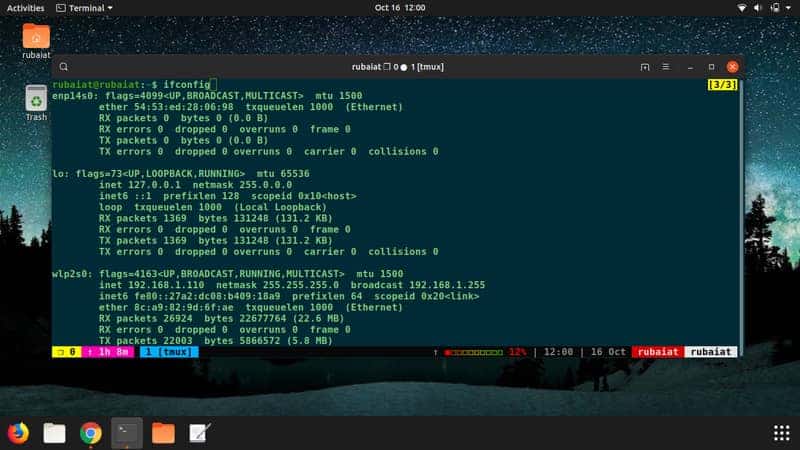
1. ifconfig
One of the most basic yet empowering network commands for Linux system administrators is ifconfig. It is a built-in system utility that allows users to configure and manage network interface parameters.
The name ifconfig stands for “interface configuration“, and it’s the go-to tool for checking whether your network interfaces are performing correctly.
$ ifconfig
Calling it without any options will provide detailed information on network devices, configuration, and current settings.
You can use the -s flag for getting shorter, more concise information. Other additional options enable ifconfig to perform more demanding tasks. Consult the man page for notes on how to use them.
2. iwconfig
The iwconfig configures wireless network interfaces like network cards and stuff. It can be used for setting up various wireless network parameters, such as the SSID access point and frequency.
Suppose you have identified your wireless interface as wlp2s0 by using ifconfig. The below command will provide network information related to this interface.
$ iwconfig wlp2s0
Use the below command to change the transmission power to 20.
$ iwconfig wlp2s0 txpower 20
Run iwconfig again to see if there is a change in transmission power. Consult the man page for additional useful options.
3. ifstat
The ifstat command is a handy utility that allows sysadmins to read and monitor network interface statistics like bandwidth usage. The below command will give you the sample statistics every SECS second.
$ ifstat --scan=SECS
The following command will report the average over the last SECS seconds.
$ ifstat --interval=SECS
The next one will output any errors.
$ ifstat --errors
This tool is part of the iproute2 project and has many additional options. Check out the man page for more queries.
4. ethtool
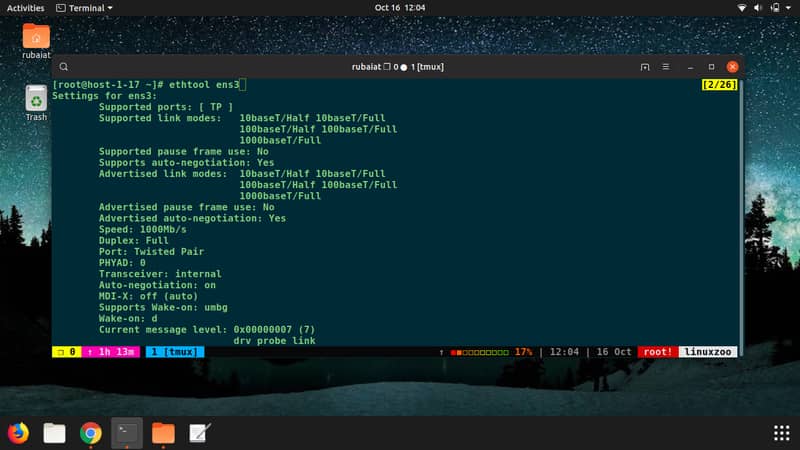
The ethtool utility allows admins to display and modify the different parameters of network interface controllers and their device drivers. It can be useful for identifying and diagnosing your ethernet devices and allows you to control the speed, duplex, and flows conveniently.
$ ethtool eth0
The above command will output the current parameters of the network port eth0.
$ ethtool -s eth0 speed 1000 duplex full
This command forces the speed of network interface eth0 to be 1000 and sets up a full-duplex. You can find many additional options by going over the manual.
5. arpwatch
The arpwatch utility is a robust ethernet activity monitoring tool that allows system administrators to keep track of the ethernet/IP address pairings of their network easily. It can be extremely important to enterprise sysadmins and Linux power users.
You can use arpwatch to watch a specific network interface using the -i flag, as shown below.
$ sudo arpwatch -i eth0
arpwatch writes any changes or unusual activities to IP or MAC to /var/log/messages. Use the tail command on this file to get new information about your ARP traffic. Consult the man page to explore more available options.
6. bmon
The bmon command is arguably among the most useful Linux network commands. It is a portable bandwidth monitor and rate estimator that can capture and display network statistics in a human-readable format.
The programmable text output provided by this Linux network monitoring tool can be used for building advanced scripts.
$ bmon
Simply invoking this tool will give you a real-time estimation of your network statistics. Use the -p flag to get output for a specific interface.
$ bmon -p wlp2s0
There are many more options available — check the man page for comprehensive details.
Linux Network Commands for Communication
Communicating with external resources is the primary purpose of system networks. This section looks at some common Linux commands used for this purpose.
7. telnet
The telnet protocol is the fundamental mechanism behind bidirectional, interactive, and text-oriented communication in Linux systems. Utilizing this communication protocol, the Linux telnet utility allows a host system to connect to another client system. Enter telnet in your terminal to invoke the interactive shell.
$ telnet
Now, enter open followed by the hostname/IP of the system you want to connect to in this shell. Enter help to get a list of all available options.
telnet> open example.com
Alternatively, you can use this command to connect with a host directly. See the below example.
$ telnet host-machine
Just type in the user credentials in the prompt, and you’re ready to go.
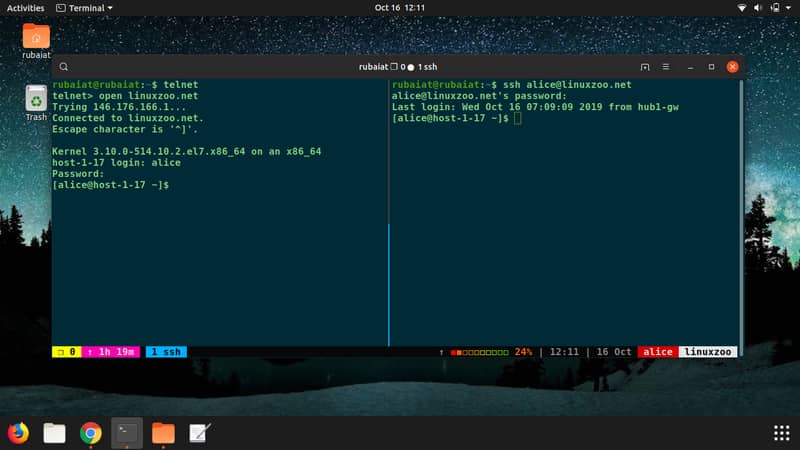
8. ssh
The ssh command is without any doubt, among the most used Linux network commands for many admins. It provides an interface to the secure shell protocol and allows hassle-free communication over a secure network connection. It can be used to manage remote servers effectively and transfer files in a trouble-free manner.
$ ssh user@host-machine
You can set up private/public key pairings and log into remote machines without typing in passwords. Use the below command to generate your ssh-key.
$ ssh-keygen
By default, the above command generates the keys using the RSA cryptographic algorithm. Use the -t flag to use other algorithms like DSA.
9. sendmail
The sendmail command is a handy utility that enables Linux users to send email messages directly from their terminals. It reads the standard input and sends emails to specified recipients over the network. This command is often useful for remote servers without a standard browser to send emails.
$ echo "Subject: Test" | sendmail [email protected] < mail.txt
The above command will send the contents of the given file to the specified email. There are a bunch of additional options you can use with sendmail. Consult the man page for more queries on sendmail.
10. write
The ability to send messages between different system users is crucial for multi-user systems such as Linux. The write command can be used for establishing terminal-to-terminal communication sessions in Linux. It is an interactive utility, and thus, using this network command inside scripts is not feasible.
$ write user [tty]
The write command takes the syntax mentioned above and sends messages to specific or all users. It will come in handy when multiple users operate the same system and need to communicate effortlessly.
11. mail
The mail command is an essential utility for sending emails from the terminal. Notice the below example to understand how it works.
$ mail -s "This is the subject" [email protected] < mail.txt
The -s flag enables users to select their subject. You can send emails to multiple recipients at the same time, as shown next.
$ mail -s "This is the subject" [email protected], [email protected] < mail.txt
Simply use a comma-separated list of recipients. The -a flag allows users to send attachments with their mails.
$ mail -s "Subject" -a /tmp/file.pdf [email protected] < mail.txt
12. mailstats
Sometimes, you may want to list your email statistics for several reasons. The Linux mailstats command will let you do this very easily. This command needs to be run as root, or it will not work.
# mailstats -p
This command will give output in program-readable mode and will provide clear statistics.
# mailstats -f STAT-FILE
This command will read the specified STAT-FILE instead of the default sendmail statistics file. Check out their man page for more available options and proper usage of the command.
13. w
The w command provides a handy way to list every user currently logged into a Linux machine. Its syntax is shown below.
w [options] user [...]
This command also provides many valuable insights like the processes running in each user’s session, emote host, login time, idle time, JCPU, PCPU, etc.
$ w --short
This command will provide a concise output omitting the login time, JCPU, or PCPU times.
$ w --ip-addr
This command will try to show the ip address of the users currently logged in instead of their hostnames. You can find more options in the manual page.
Network Commands for Facilitating Data Transfer
Transferring data across several systems is mandatory for sysadmins. Linux facilitates remote data transfer over a network conveniently and offers robust command-line tools. In this section, we take a look at some of these commands.
14. cURL
The cURL command is one of the most widely used Linux commands for transferring data to or from a network server. It utilizes various network protocols such as HTTP, HTTPS, FTP, FTPS, SCP, SFTP, etc. The cURL command doesn’t require user interaction and can be used extensively inside shell scripts.
$ curl -O https://somedomain/file
This will download the file from the specified address and save it in the current directory with its original name.
$ curl -o new-name https://somedomain/file
This command saves the downloaded file with the name new-name. Since cURL has a plethora of available options, checking out the manual is a must if you want to master this Linux tool.
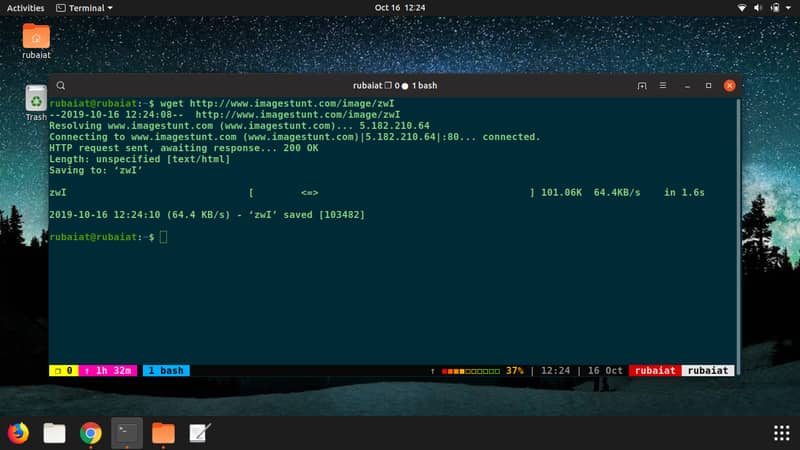
15. wget
The wget tool is part of the GNU project and facilitates downloading content from web servers. It offers several useful options, including recursively downloading files, converting links to HTML for offline viewing, proxies, etc.
$ wget https://somedomain/file
This downloads the file and saves it to the current directory. Use the -O flag to save this file under a new name.
$ wget -O filename https://somedomain/file
Use the -P flag to save the file in some other directory.
$ wget -P ~/Downloads https://somedomain/file
wget is non-interactive and is used extensively for downloading files from inside scripts.
16. ftp
The Linux FTP utility is widely used for downloading or uploading files to/from remote hosts. This command can be used inside scripts to create automated FTP sessions quickly.
$ ftp ftp>
Simply typing ftp in the terminal creates an interactive session. You can enter various commands in this prompt for transferring files over FTP.
For example, you can use the open common for connecting to a remote host. Enter the help command to get a list of all the available commands.
$ ftp hostname
You can also use it to connect to remote hosts directly. See the man page for detailed information on all available commands.
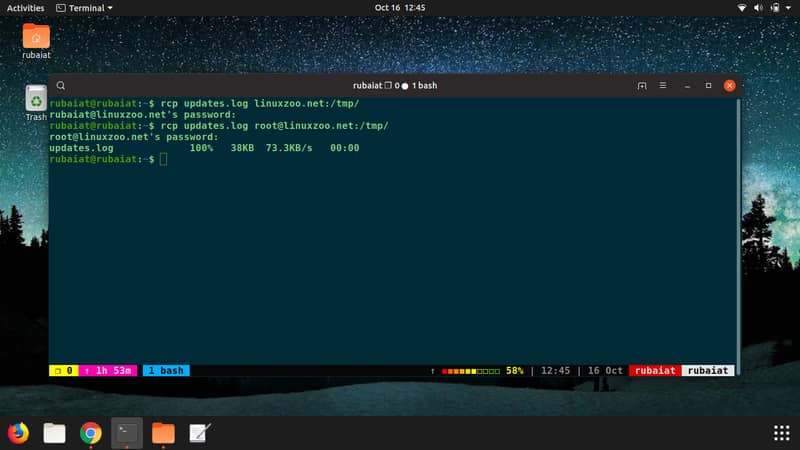
17. rcp
The rcp utility allows users to copy files or directories from their local system to a remote machine on the network. The command has a syntax like below.
rcp [options] SOURCE DESTINATION
For example, the next command shows how to copy a file called test.doc to a remote machine.
$ rcp /parent/dir/test.doc hostname:/some/dir
You can also use this command to receive files from a remote host, as shown below.
$ rcp hostname:/some/dir/FILE
Simply omit the source portion when receiving files.
18. scp
The scp (secure copy) command is used for copying files securely between two network systems. It is similar in functionality to the rcp command but implements secure authentication like the ssh command. This handy command lets you copy both files and directories to remote machines.
$ scp FILE username@remote-host:/some/dir
The above command copies FILE to the remote system’s /some/dir directory. If the remote host is listening to some other SSH port instead of 22, you can use the -P flag to specify that.
$ scp -P 2222 FILE username@remote-host:/some/dir
We encourage you to check the man page of scp to explore additional options and their use cases.
19. rsync
The rsync utility transfers and synchronizes files efficiently between two systems connected via a network. Sysadmins often use it to transfer files from external NAS servers to their local machine. It is a high-speed and reliable tool for copying files to and from remote computers.
$ rsync -zvh backup.tar /tmp/backups/
The above command synchronizes a file called backup.tar to the temporary directory. It uses the -z option to compress the file data, -v to get verbose output, and -h to get human-readable output. It also allows access via remote shell and the rsync daemon. Consult the man page to learn their usage.
20. socat
The Linux socat tool is used for establishing two bi-directional byte streams and allows the transfer of data between them very efficiently. The socat command is one of the most versatile Linux network commands and has diverse use cases.
$ socat SYSTEM:date STDIO
This command takes the current system date and prints it to the standard input.
$ socat - TCP:localhost:www,crnl
The above command opens a web server connection to the localhost and fetches a page to the terminal. Notice how the port number has been passed as a service name. This is a very robust command and supports many short forms. So, check out their man page to master them effectively.
21. sftp
The sftp command is used for accessing, transferring, and managing files using the secure file transfer protocol. It allows admins to use FTP over a secure shell. If you can use ssh and ftp commands, then using sftp will be very easy.
$ sftp user@hostname
This command opens a secure connection and starts the FTP prompt. It establishes the connection on the default SSH port (22). Since many sysadmins use custom port numbers for ssh to avert malicious users, you need to pass that port number to connect to such systems.
$ sftp -oPort=CUSTOM-PORT user@hostnameems
Read the man page to explore all possible options and their usage.
22. sshfs
The sshfs command is arguably among the most useful Linux network commands for mounting remote filesystems. This command has a basic syntax but can be a versatile asset for modern sysadmins.
$ sshfs user@hostname:/some/dir /mountpoint
The above command mounts the remote filesystem to the specified mount point. Note that the user must own the mount point for this command to work. The remote filesystem will be automatically unmounted when you close the connection. You can make it permanent by editing the /etc/fstab file.
Network Commands for Administrating Network Policies
Admins can easily set up different policies for their Linux machines and networks with some powerful Linux network commands. Some of these tasks include but are not limited to setting up device drivers, configuring routing policies, managing tunnels, and so on. This section looks closely at some of the commands that facilitate these jobs.
23. hostname
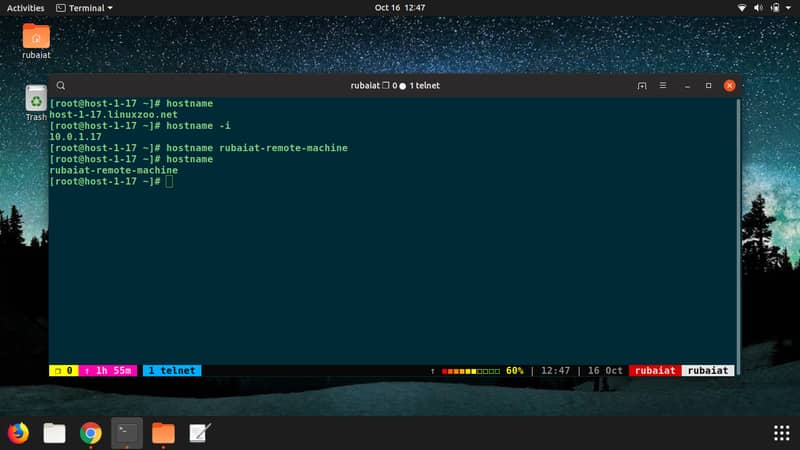
The hostname command is a handy utility that allows admins to get or set hostname or DNS domain names. It is often used to set up dynamic hosts or get information on a specific host. Simply typing your hostname in the terminal will show your current hostname.
$ hostname
The next command will replace your current hostname with NEW_HOST_NAME.
$ hostname NEW_HOST_NAME
The -i flag can be used to get the current IP address of your hostname.
$ hostname -i
There are more options you can use with this command. Consult the man page for detailed information on them.
24. iptables
The Linux iptables command is, without any doubt, one of the most used Linux network commands for sysadmins. The iptables program is a user-space utility program that allows admins to configure the iptable chains and set up firewalls. It is a de facto tool for preventing unauthorized or malicious traffic to your network.
$ sudo iptables -L -n -v
The above command will print out the current iptables rules used by your system. The next command shows you how to block all incoming requests from a specific IP.
$ sudo iptables -A INPUT -s xxx.xxx.xxx.xxx -j DROP
There are many possible iptables commands; you can find comprehensive details in this post.
25. route
You can use the route command to view and manipulate your system’s IP routing table. It allows admins to easily edit the kernel routing tables and set up desired functionalities. This command is also available in Microsoft Windows systems and is thus used very extensively.
$ sudo route -n
This command will list the current IP routing table. The next command shows you how to add a default gateway for your machine.
$ sudo route add default gw xxx.xxx.xxx.xxx
You can verify the new gateway using the earlier command. Check out the manual page for a comprehensive list of all available options.
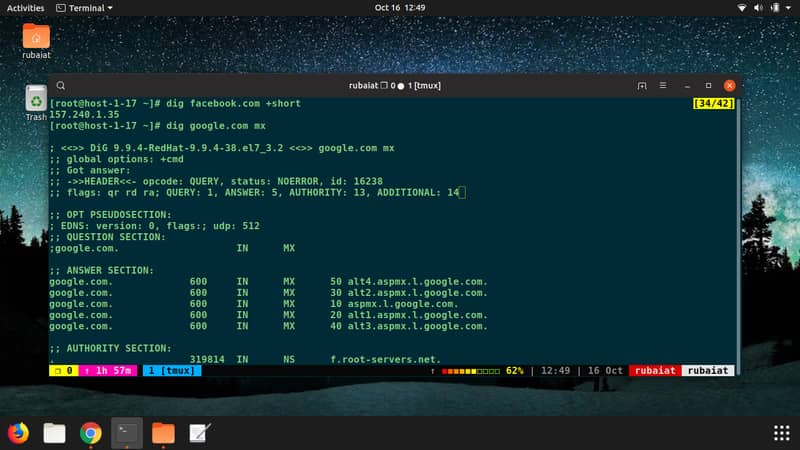
26. dig
The dig command allows admins to query the Domain Name System (DNS) for network troubleshooting and other purposes. Dig utilizes the default DNS resolver of your Linux machine and supports Internationalized domain name (IDN) queries.
The below example demonstrates how easily dig provides DNS record information for a host.
$ dig example.com
Use the +short option to get a concise output.
$ dig example.com +short
You can also query different types of DNS resource records using MX.
$ dig example.com MX
Read the man page to understand all possible use cases and available options.
27. ip
The ip command allows Linux users to quickly leverage the IP utility for manipulating the routing, devices, policy routing, and tunnels. It’s a very dynamic tool and offers numerous robust options. The below example demonstrates how to display the IP addresses of all network interfaces using this tool.
$ ip addr
You can use the short form a instead of addr. The next command shows you how to get information for only the currently running interfaces.
$ ip link ls up
The next example shows how to assign IP addresses to a specific interface.
$ ip a add 192.168.1.XXX/24 dev eth0
This command supports a wide array of additional options. So, don’t forget to check the man page.
28. nslookup
The nslookup utility is a powerful command-line tool that allows sysadmins to obtain a domain name or IP address mapping by querying the Domain Name System. It’s available in most Unix-like systems alongside Windows and ReactOS. The below command shows the primary usage.
$ nslookup example.com
It provides information like the domain name and IP address of the host. The next commands show all the available DNS records.
$ nslookup -type=any example.com
The following command will be for an MX record for the specified host.
$ nslookup -type=mx google.com
Linux Commands for Network Diagnosis and Troubleshooting
Effectively diagnosing networks is of greater concern for most sysadmins. We list some useful commands for this purpose in the following section.
29. netstat
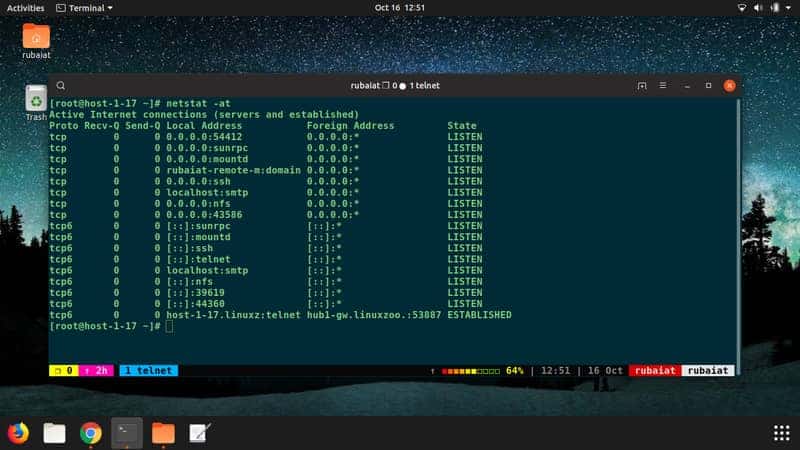
The netstat utility shows the network connections for the TCP protocol, routing tables, network interface statistics, masquerade connections, and multicast memberships. It’s one of the most widely used commands for network diagnosis.
$ netstat -a | more
The above command displays all network sockets irrespective of their current state. Use the next command only to display TCP ports.
$ netstat -at
Replace t with u if you want to list the UDP ports. The following command will display only the listening ports.
$ netstat -l
Append t or u after -l if you want to list only the listening TCP/UDP ports. Check the man page for all available options.
30. ping
In Unix-like operating systems, the ping command is frequently used to determine the reachability of a host on an Internet Protocol network. This is a universal networking command available in virtually any system. The next example shows the primary usage of ping.
$ ping example.com
This will continue to send packets to the host until you terminate it manually. Use the -c option to specify the number of packets.
$ ping -c 5 example.com
You can also determine the size of the packets using the -s flag.
$ ping -s 40 -i 2 -c 5 example.com
the -i option changes the time interval from the default 1 to 2 seconds.
31. traceroute
The traceroute command is usually used for displaying the route and measuring transit delays of packets across the network. It’s a handy tool for modern system admins and offers many essential insights. You can quickly determine the path a packet takes from its source to its destination. It is also beneficial for determining data loss.
$ traceroute -4 10 example.com
The -4 is used to specify that you are using IPv4. Replace 4 with 6 for IPv6 packets.
$ traceroute -g xxx.xxx.xxx.xxx example.com
The above command routes the packets through the specified gateway. Check the man page for all available options.
32. iftop
The iftop utility is one of the most useful Linux network commands, providing real-time feedback for network parameters such as bandwidth usage. If you’ve used top or htop, iftop will feel quite similar. Due to its immense usefulness, this tool can be a viable asset to modern-day Linux users.
$ sudo iftop
Running this command as sudo will provide you with the current bandwidth usage by your network interfaces. You can specify which interface to monitor by giving the -i flag.
$ sudo iftop -i wlp2s0
It will show information about the wireless interface only. There are plenty of other options available.
33. nload
The nload utility is another command-line tool for monitoring your network bandwidth. It features some advantageous abilities, such as displaying the total amount of transferred data and min/max bandwidth usage. Directly invoking nload without any arguments will show the bandwidth usage of each available interface.
$ nload
Use the devices options to specify a particular interface, as shown in the example below.
$ nload devices wlp1s0
You can also use the -t flag to set the refresh interval of the display in milliseconds.
$ nload devices wlp1s0 -t 400
34. ss
The ss command provides useful information related to network sockets. It can display much more detailed information compared to other Linux monitoring tools like netstat. Directly calling ss from the terminal presents a vast list of all the connections regardless of their state.
$ ss -l
You can specify to list only the listening sockets using the -l flag. The -t flag is used to show only TCP connections.
$ ss -lt
Use the -p flag to get the process id of the active sockets, as shown below.
$ ss -p
You can find more available options on their man page.
35. whois
The whois utility is a widely used Linux tool for obtaining both domain and IP-related information about a network. It works as a client for the whois protocol and provides information by querying the whois databases for network resources.
$ whois example.com
The above command will print out detailed network resource information about the specified host. Since this command provides a lot of information, you can use grep for getting specific data.
$ whois example.com | grep -i "Domain ID"
The above command will output the lines that contain the Domain ID of the specified host. You can also use it for additional information like name servers and domain status.
Network Commands for Analyzing Resources
Analyzing network packets is extremely important for both sysadmins and penetration testers alike. In this section, we go over some fundamental Linux commands that allow doing this efficiently.
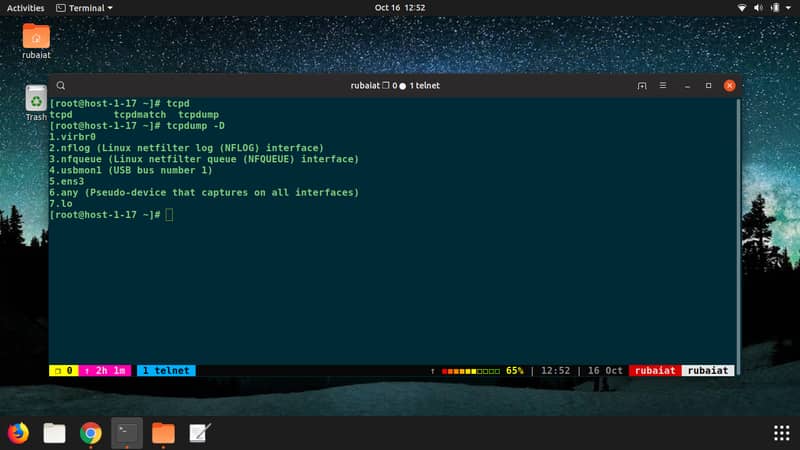
36. tcpdump
The de-facto command-line packet analyzer for Linux is tcpdump. It can display the transmission of TCP packets over the network very effectively. It is commonly used for capturing and analyzing network traffic due to its universal availability.
$ sudo tcpdump -D
The above command displays which interfaces are available for capturing TCP packets. You can easily capture packets from a specific interface by the following command.
$ sudo tcpdump -i eth0
This will only capture packets transmitted through the default ethernet interface. Check out the man page to explore all possible options.
37. dhclient
The dhclient utility is a robust DHCP (Dynamic Host Configuration Protocol) client. It is frequently used to analyze a client’s IP address, subnet mask, default gateway, and DNS server information. It also allows admins to release the IP address of a specific network interface and obtain new ones.
$ sudo dhclient eth0
The above command will renew the dynamically assigned IP address of the ethernet interface eth0.
38. dstat
The dstat utility is an extremely rewarding command-line tool for generating system resource statistics in Linux. It offers numerous robust functionalities and can be easily extended using Python programming language. It is a worthy replacement for the legacy vmstat utility.
$ dstat
Running this command without any options provides a real-time display of system resource statistics. The next command outputs the CPU usage, the process using the most CPU, and the process consuming the most RAM.
$ dstat -c --top-cpu --top-mem
Consult its man page for more available options.
39. tshark
The Wireshark utility is among the most feature-rich packet analyzers. Its abilities surpass tcpdump considerably and are widely used in forensics. You can easily install it using your package manager. The command-line package is called tshark.
$ sudo tshark -D
This will list all available interfaces that can be used for capturing network traffic. The next command shows how to capture data using the ethernet interface eth0.
$ sudo tshark -i eth0
40. hping3
The hping3 command is used to invoke the hping utility. It is a powerful, modern-day packet analyzer that can efficiently capture and analyze/assemble TCP packets. It is available on most Unix systems, including Linux and BSD.
# sudo hping3
It will start the interactive hping3 session where you can type in commands. The next command captures TCP traffic from the eth0 interface.
> hping recv eth0
You can also use hping outside its interactive shell. Consult the man page to learn how to do this.
Ending Thoughts
The robust networking abilities of Linux have contributed largely to its present-day success. No matter what type of networking tool you want, Linux has got you covered.
However, the plethora of Linux network commands can make it quite difficult for many users to choose the right tool. That’s why our editors took the liberty of pointing out these 40 useful commands for you.
You can find at least one tool for any networking activity. Hopefully, we could provide the essential insights you were looking for. Leave us a comment if you want to explore some commands in more detail.

Two more:
arping – ping using arp (MAC address). This helped me find an IP address collision on a network (duplicated IPs)
tcptraceroute – traceroute using TCP packets. This can be helpful where the regular traceroute packets are blocked.
ip on #27 and ifconfig on #1, really? Ifconfig and friends are deprecated for years now.
It’s a generic list, not following any particular sequence.
Iperf network bandwidth and loss analyzer