Fail2ban is an internet security utility tool for Linux server and web-host admins. You can use the Fail2ban tool to control, monitor, and add rules on your Linux server. Suppose you have a website on any hosting platform. In that case, you might know that if you enter the wrong username or password rapidity, the system automatically prevents you from login into your WHM or c-Panel, and dashboard. If you have a server running under a Linux system, you can maintain your server’s login monitoring system using the Fail2ban tool. I must say, if you are a Linux server admin, installing Fail2ban is an excellent attempt to make your server secure, safe, and stable.
Important Features of Fail2ban
Fail2ban is written in Python that can prevent your Linux server from brute-force attacks.
After you get an attack, you can check the strength of that attack from the Fail2ban log file. You may ask, can Fail2ban prevent the DDOS attacks on your server? The answer is, Fail2ban is not designed to avoid the DDOS attacks; it is made to prevent the unknown or suspicious login attempts.
But, definitely, the Fail2ban can reduce the number of DDOS attacks on your Linux server. Once you install the Fail2ban tool on your Linux server and set the parameters, it can automatically protect your server from login attacks.
Fail2ban uses the Jail script to make the Linux server secure. Jail is the settings script file, where all the default IP blocking and maintaining parameters are set. Understanding the Jail script is essential to ensure the security of your Linux server.
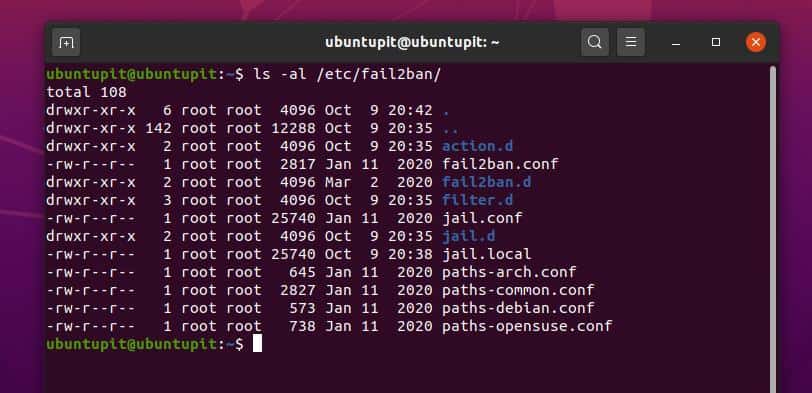
To see the configuration files of Fail2ban, run the following list command on your terminal. You will find a fail2ban.conf and a jail.d file inside the list. We will work in the jail.d file to re-configure the Fail2ban settings.
ls -al /etc/fail2ban/
I am listing the primary and basic features of the Fail2ban tool on the Linux system.
- Supports Python Scrapy
- Block IP for a Specific Range
- Global Timezone Wise Block
- Customized Parameter Settings
- Easy to Configure with Apache, Nginx, SSHD, and other Servers
- Receive an E-mail Alert
- Ban and UnBan Facilities
- Set Ban Time
Fail2ban on Various Linux Distributions
Linux enthusiasts must know that Linux powers most of the web-servers. While servers are powered on Linux, it is mandatory to maintain a very tight security benchmark to block unauthorized login attempts. In this post, we will see how to install and configure the Fail2ban package on various Linux distributions. Later, we will also see how to modify and observe the Fail2ban tool.
Step 1: Install Fail2ban Package on Linux
Installing Fail2ban on Linux is a straightforward process. You need to update your system repository and install the package directly with a few terminal command-lines. I will go through the installation methods of Fail2ban on Debian, Fedora Linux, Red Hat Linux, OpenSuSE, and Arch Linux.
1. Install Fail2ban on Ubuntu and Debian Distributions
In Debian distributions, updating the system repository is the process to make your Linux system smoother and more efficient. As we will install a new package on our system, we must first update the system repository. You can use the following command lines to update your system repository.
sudo apt update
sudo apt upgrade -y
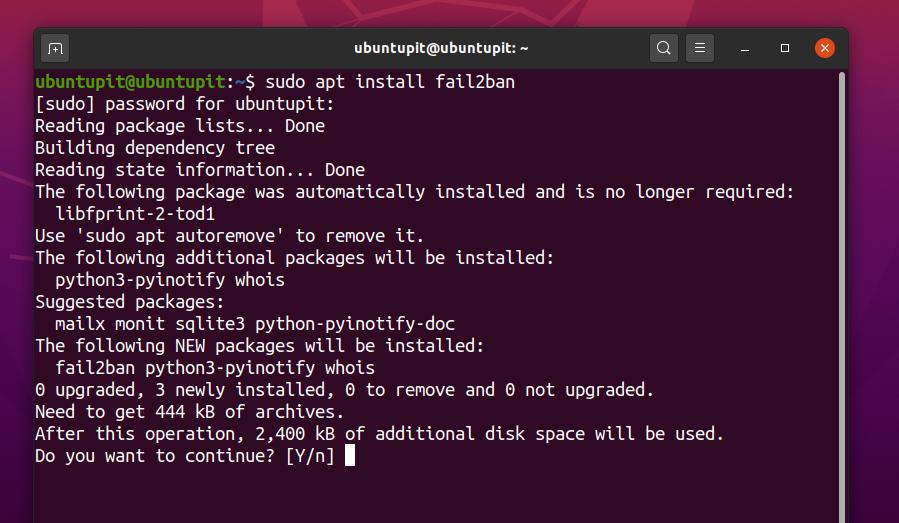
Now, copy and paste the following aptitude package management command to install the Fail2ban tool inside your Debian system. You can use this command for Ubuntu, Kubuntu, Linux Mint, and other Debian distributions.
sudo apt install fail2ban
2. Install Fail2ban in Manjaro
Here, we have chosen the Manjaro Linux to show how you can install the Fail2ban package on Arch and Arch-based Linux distributions. Manjaro is supported and maintained by the Arch Linux project. You can use the following packman command-line to install the Fail2ban on your Arch Linux.
sudo pacman -S fail2ban
If you face any error while installing the package, you can run the following -Rs command in your Arch Linux terminal to bypass the error.
sudo pacman -Rs fail2ban
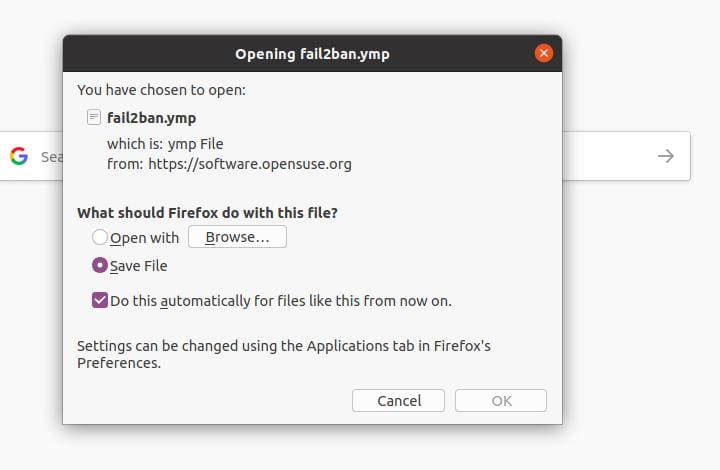
3. Install Fail2ban in OpenSuSE and SuSE Linux
In SuSE and OpenSuSE Linux, installing Fail2ban is much easier than other distributions. First, you need to download the .ymp package file of Fail2ban. You can download the Fail2ban package for SuSE Linux from here. Once the download is finished, open the package file through the default software store of SuSE Linux. Then click on the install button to complete the installation process.
4. Install Fail2ban on Fedora
Here, I will show you how to install the Fail2ban package on Fedora Linux. I am using the DNF command to install the package on Fedora. First, install the extra packages for enterprise Linux (EPEL) release on your system.
sudo dnf install epel-release
Now, run the following command on your Fedora Linux terminal to get the Fail2ban package.
sudo systemctl start sshd
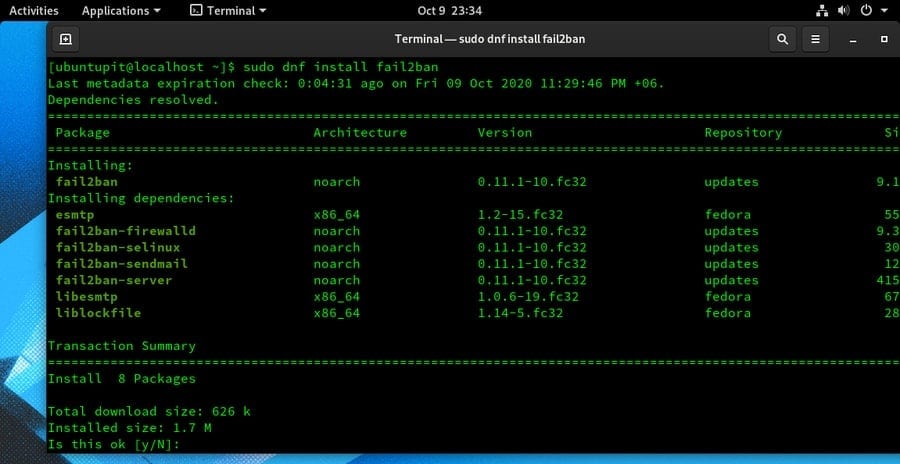
sudo dnf install fail2ban
5. Install Fail2ban on CentOS and Red Linux
Very rarely, people use Red Hat and CentOS to maintain a server. However, if you have a server installed on your Red Hat Linux, you can install the Fail2ban package on your Linux system by running the following yum commands on your Linux machine.
First, install the Extra Packages for Enterprise Linux (EPEL) release on your system. Then install the Fail2ban package.
sudo yum install epel-release
sudo yum install fail2ban
Step 2: Firewall Settings on Linux
As Fail2ban uses a network protocol to maintain the Linux server, you need to make sure that your Linux firewall is enabled and configured to access the Fail2ban package. By default, Fail2ban uses port 22 to establish the connection. That’s why you need to allow port 22 for Fail2ban. Here, we will see how you can set the Firewall settings for Debina and other Linux distributions.
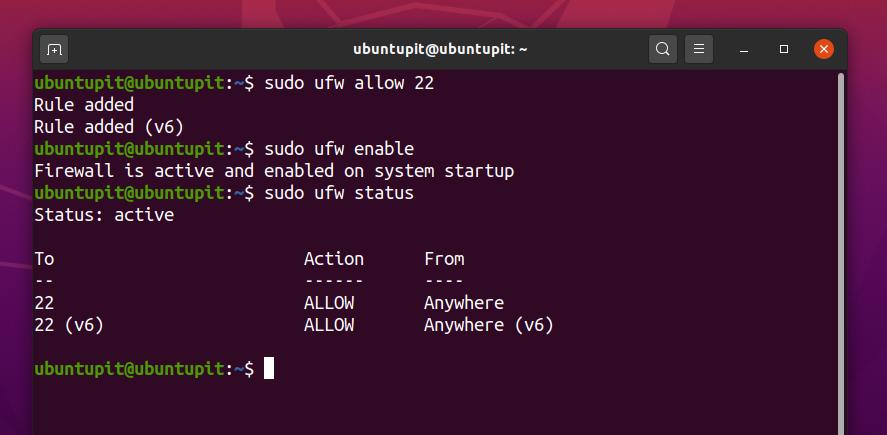
1. Firewall Settings for Ubuntu and Debian
Debian and Ubuntu users can enable the UFW settings to add the firewall rule. Follow the terminal command-lines to configure the UFW firewall on your Debian distributions. If the Firewall is not enabled on your Debian system, enable it first.
sudo ufw allow 22
sudo ufw enable
Now you can check the firewall status on your Linux system. You will find that port 22 is added and allowed on the firewall setting.
sudo ufw status
2. Firewall Settings for Red Hat, CentOS, and Fedora Linux
Red Hat, Fedora, Centos, Arch Linux, SuSE, and other Linux distributions use the Firewalld tool to configure the firewall settings. As we know that UFW is a dedicated command-line based firewall interface for Debian distributions, in the same way, Firewalld is the primary application programming interface (API) management tool where you can add firewall rules.
You can use the following system control commands to start, enable, stop, and reload the Firewalld on your Linux machine.
systemctl status firewalld
systemctl enable firewalld
sudo firewall-cmd --reload
systemctl stop firewalld
As we already know that we have to allow port 22 on the firewall configuration. Use the following commands to add the rule. You can also use the zone-based configuration system on the Firewalld tool.
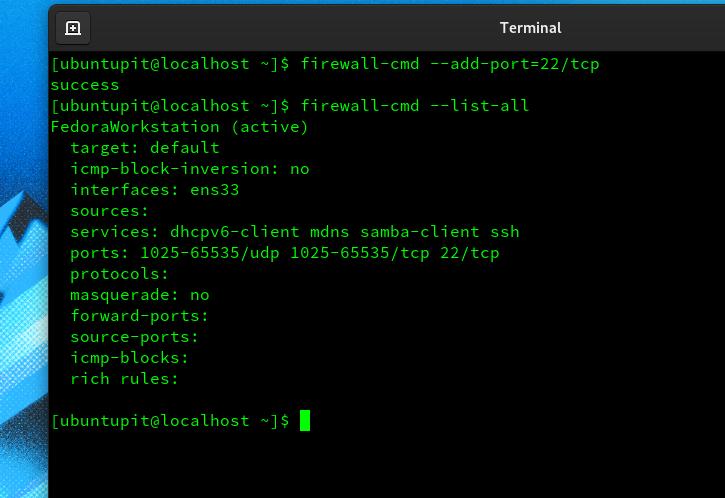
firewall-cmd --add-port=22/tcp
firewall-cmd --list-all
Now, restart the Fail2ban tool on your Linux system.
systemctl restart fail2ban
Step 3: Configure Fail2ban on Linux
Till now, we have installed the Fail2ban and configured the firewall settings. Now, we will see how to configure the Fail2ban settings. The general settings and configurations are the same for all Linux distributions. You can follow this step for all distributions.
First, you have to configure the Jail settings on Fail2ban. You can keep the default settings if you don’t need to make any changes. You can find the configuration script in the /etc/fail2ban/ directory. Use the following terminal command-lines to edit and configure the Jail settings.
cd /etc/fail2ban/
sudo cp jail.conf jail.local
sudo nano /etc/fail2ban/jail.conf
Now, you can copy and paste the following rules inside your Jail configuration script. Here, we are settings the bantime, ignoreIP, findtime, and maxretry parameters.
[DEFAULT]
ignoreip = 127.0.0.1
bantime = 3600
findtime = 600
maxretry = 3
[sshd]
enabled = true
ignoreip = 127.0.0.1 ::1 192.168.100.11
I am giving a concise description of the Fail2ban script parameters.
- bantime – Bantime is the time duration that you want to apply to ban any suspicious IP address.
- ignoreip – The ignoreip is referred to as the IP address that you want not to ban or monitor by the Fail2ban tool. Typically your current host IP, personal IP address, and localhost addresses are added inside the ignoreip list.
- maxretry – Maxretry is a type of log file that stores the failed login attempts on your Linux server. You can control how many tries you want to allow any user to log in.
- findtime – Findtime is the past time duration that you can add to the setting to find to crosscheck the suspicious IP addresses.
You can also unban any IP addresses from your Fail2ban settings on Linux. First, you need to open the SSHD configuration script of Jail. Then you can unban the desired IP address.
/etc/fail2ban/jail.d/sshd.local
Use the following command lines to unban any IP address.
/etc/fail2ban/jail.local
sudo fail2ban-client set sshd unbanip 83.136.253.43
Step 4: Monitor Fail2ban Status
Once the installation and configuration steps are done, you can now monitor the Fail2ban work functions from your Linux system. Here, I will describe a few basic command-lines that you can run on your Linux terminal to watch and monitor the Fail2ban tool.
You can use the following command line to see the debug info, trace info, ping, and other related information about the Fail2ban tool.
fail2ban-client -vvv -x start
Use the following terminal command-lines to view the log file and authorization files of the Fail2ban from your Linux system.
nano /var/log/fail2ban.log
nano /var/log/auth.log
Use the following command-lines to monitor the client’s status and SSHD status of the Fail2ban.
sudo fail2ban-client status
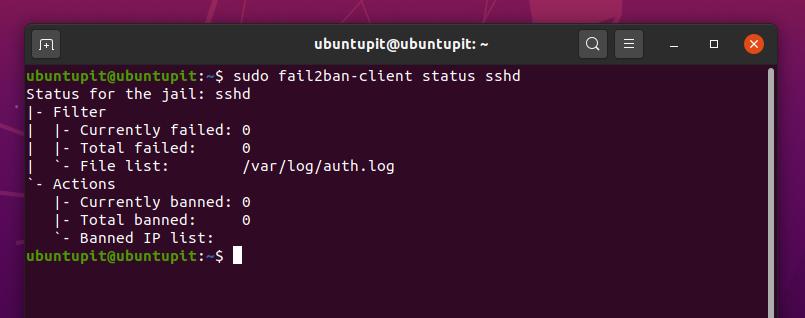
sudo fail2ban-client status sshd
To view the banned IP log, run the following terminal command-line in your Linux shell.
sudo zgrep 'Ban:' /var/log/fail2ban.log*
To view the error log file, run the following terminal command-line in your Linux terminal.
/var/log/httpd/error_log
You can check the status of the Fail2ban through the system control command lines. Use the terminal command-lines given below to check the Fail2ban status on the Linux system.
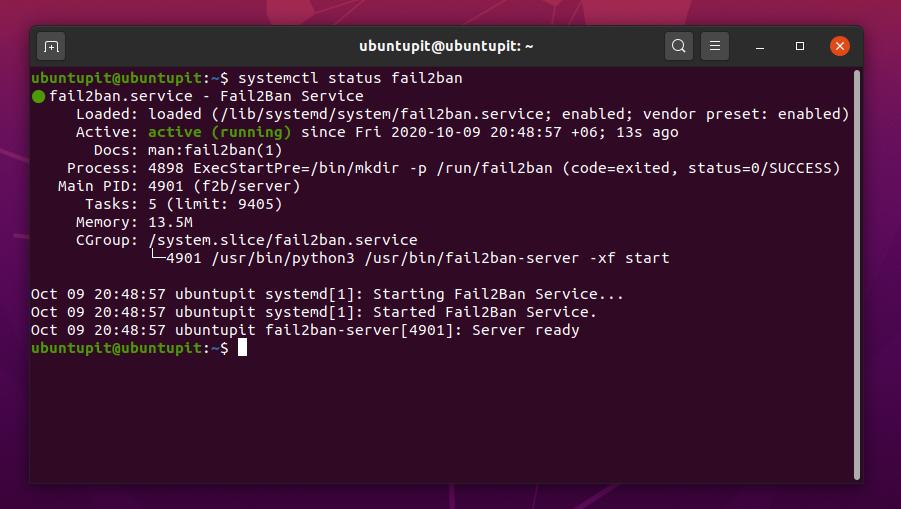
systemctl status fail2ban
systemctl status fail2ban.services
You can run the Fail2ban services on your system startup. To add the Fail2ban package on your startup application list, use the following system control command-line on your Linux terminal.
systemctl enable fail2ban.services
Lastly, you can use the following terminal command-lines given below to start, restart, and enable the Fail2ban services on your Linux system.
systemctl enable fail2ban
systemctl start fail2ban
systemctl restart fail2ban
Extra Tip: Get Email Alert
This step will show how you can get an email alert when someone tries to log in to your Linux server from an unauthorized device, using the wrong username or password, and malicious network. To set the email alert settings, you need to edit the jail.local file from the Fail2ban directory.
First, you can make a copy of your Jail setting script so that you can replace the default settings if you do anything wrong. Run the following command-line to make a copy of the Jail script.
sudo cp /etc/fail2ban/jail.conf /etc/fail2ban/jail.local
You can use the following command-line given below to edit the jail.local configuration script.
sudo nano /etc/fail2ban/jail.local
Now, copy and paste the script-commands given below inside your jail.local script. Then replace the destination email (destemail) and the sender email address on the script. Then you can save and exit the configuration script.
[DEFAULT]
destemail = [email protected]
sender = [email protected]
# to ban & send an e-mail with whois report to the destemail.
action = %(action_mw)s
# same as action_mw but also send relevant log lines
#action = %(action_mwl)s
Now restart the Fail2ban tool on your Linux system.
sudo systemctl restart fail2ban
Remove Fail2ban from Linux
Removing Fail2ban on Linux distribution requires the standard method of uninstalling packages from Linux. Now, I am going to show how you can remove the Fail2ban tool from your Linux system. Use the following command-lines to remove the package from Debian/Ubuntu Linux system.
sudo apt-get remove fail2ban
Use the following command-lines to remove the Fail2ban from Fedora, CentOS, Red Hat Linux, and other Linux distributions.
sudo yum remove fail2ban
sudo yum purge fail2ban
sudo yum remove --auto-remove fail2ban
Ending Words
No doubt, Fail2ban is an essential tool for the Linux system and server administrators. While using UFW, IPtables, and other network monitoring tools helps server managers, the Fail2ban is a complete package that can prevent anonymous logins from harmful or anonymous users.
In the entire post, I have described the methods of installing, configuring, and monitoring the Fail2ban tool on various Linux distributions. Please share this post with your friends and Linux server admins if you find this post useful and informative. You can write down your opinions regarding this post in the comment section.