The OpenSSH suite is a collection of robust tools intended to facilitate the remote control and transfer of data between networked systems. It consists of a number of tools, including SSH, SCP, SFTP, SSHD, and many more. Every time you use ssh to log in to a remote machine, you are highly likely to leverage the OpenSSH server. In this guide, we will provide an in-depth discussion on how OpenSSH works and how to utilize it properly for meeting growing security demands. So, if you want to learn more about the intricacies of OpenSSH, stay with us throughout this guide.
Deep Dive into OpenSSH Server & Services
The OpenSSH server sits at the heart of remote communication between Linux and/or BSD machines. Some of its notable features include traffic encryption, several powerful authentication methods, secure tunneling, and sophisticated configuration abilities. The below sections provide a meaningful understanding of the fundamental services and security tips.
The Fundamentals of an OpenSSH Server
As suggested by its name, OpenSSH utilizes the SSH (Secure Shell) protocol for providing remote connection and data transfer facilities. It removes the security vulnerabilities associated with legacy methods such as the Linux FTP command and telnet. OpenSSH makes it easy to authenticate legitimate users and to encrypt remote connections.
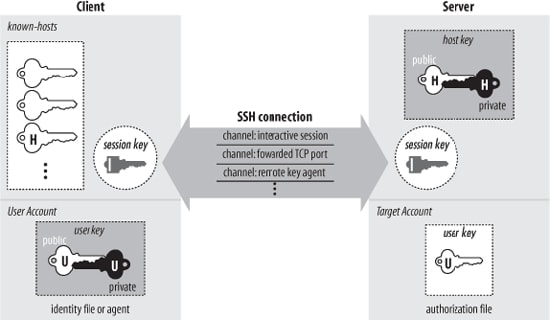
The core utility of the OpenSSH suite responsible for managing remote connections is the OpenSSH Server or sshd. It constantly listens for incoming requests and sets up the appropriate connection type when a new request comes in.
For example, if a user uses the ssh client program to communicate with the server, sshd will set up a remote control session as soon as the authentication is successful. If the user uses SCP instead, sshd will initiate a secure copy session.
The end-user need to choose the appropriate communication mechanism for their connection. This is facilitated by tools such as ssh-add and ssh-keygen. When a user successfully connects to the remote machine using the ssh command, he is greeted by a text-based console. Any commands entered on this console are sent over an encrypted SSH tunnel for executing on the remote machine.
Installing and Configuring OpenSSH Server
The following section will discuss how to install the OpenSSH server daemon and configure it. We will show the best configuration options for both personal use and enterprise purposes. We will also outline the best practices for configuring and hardening OpenSSH at the end of this section.
How to Install OpenSSH Server
Most modern Linux distributions come with OpenSSH already installed. However, if you need to install it manually, you can do it using the following simple command.
$ sudo apt install openssh-server
This command will install the server daemon. Use the below command to install the OpenSSH client in your system.
$ sudo apt install openssh-client
How to Configure OpenSSH Server
OpenSSH supports a large number of configuration options for controlling things such as communication settings and authentication modes. The sshd_config file specifies the configuration parameters and holds the address of other config files, including one or more host key files and authorized_keys files. It is located in the /etc/ssh/ directory of your filesystem.
Before moving on to tweak some of its parameters, we suggest you back up the current copy of the sshd_config file. You can do this by opening up your favorite Linux terminal emulator and issuing the following command.
$ sudo cp /etc/ssh/sshd_config /etc/ssh/sshd_config.bak
This way, if you mess up your sshd_config file, you can always revert to the original configuration. Now, you can proceed to configure your ssh server. Before that, we suggest readers test their effective sshd configuration by using the below simple command.
$ sudo sshd -T
Now that you have backed up your sshd_config file and viewed the default settings, it is time to edit the configuration file. We will use the vim text editor to open and edit our config file. But, you can use any Linux text editor you want.
$ sudo vim /etc/ssh/sshd_config
As you should notice, there are already a number of pre-configured options. However, most of them are commented out. You can activate them by uncommenting the particular line that specifies the options parameter. Remove the pound “#” symbol from the beginning of a line to uncomment it. We discuss some of the important options below.
- AcceptEnv
This option specifies which environment variables sent by the client can be copied to the remote environment.
- AddressFamily
Defines the IP address family for sshd’s use. The three available options are – any, inet, and inet6.
- AllowAgentForwarding
This option defines if ssh-agent forwarding is permitted or not.
- AllowStreamLocalForwarding
Defines if the forwarding of Unix domain sockets is allowed or not.
- AllowTcpForwarding
Defines if TCP forwarding is allowed or not.
- AllowUsers
This option can define a list of user names that are allowed access based on a pattern. All user names are allowed by default.
- AuthenticationMethods
This option states the authentication methods a user must complete before receiving access.
- AuthorizedKeysFile
This option specifies the file that contains the public keys for user authentication.
- ChallengeResponseAuthentication
When enabled, this option allows challenge-response authentication.
- ChrootDirectory
Specifies the root directory, which will be presented to users who have authenticated successfully.
- Ciphers
This option defines the cryptographic ciphers allowed by the OpenSSH server. There are a wide array of available options.
- Compression
Specifies whether compression is allowed and, if it is, at which stage.
- DenyUsers
This option can be used to define a list of user names denied access based on a pattern.
- ForceCommand
It can be used to force execute a certain command. It makes the server ignore any command provided by the ssh client and anything present in ~/.ssh/rc.
- GatewayPorts
This option defines whether remote hosts can connect to ports that have been forwarded for the client-side.
- GSSAPIAuthentication
It is used to indicate whether GSSAPI-based user authentication is allowed or not.
- HostbasedAuthentication
This option specifies whether a public key present in the client machine can authenticate a host on the remote server.
- HostbasedUsesNameFromPacketOnly
This option specifies if the server needs to perform a reverse name lookup for names present in the /.shosts, ~/.rhosts, and /etc/hosts.equiv files.
- HostKey
It can be used to define a file that contains a private host key. Admins can specify multiple key files. the default ones are /etc/ssh/ssh_host_dsa_key, /etc/ssh/ssh_host_ecdsa_key, /etc/ssh/ssh_host_ed25519_key and /etc/ssh/ssh_host_rsa_key.
- HostKeyAlgorithms
This option defines the host key algorithms made available by the ssh server. OpenSSH supports a large number of algorithms for this purpose.
- IgnoreRhosts
Tells the server to ignore the .rhosts and .shosts files for RhostsRSAAuthentication and HostbasedAuthentication.
- KbdInteractiveAuthentication
This option defines if the server allows keyboard-interactive authentication or not.
- KexAlgorithms
It is used to state the available algorithms for ssh key exchange. OpenSSH supports all major key exchange algorithms, including Diffie Hellman and Elliptic Curves.
- ListenAddress
Defines which local addresses the sshd daemon should listen to.
- LoginGraceTime
This option defines the time after which sshd disconnects the user if it fails to log in successfully.
- LogLevel
It defines the verbosity level of the log messages for sshd.
- MACs
This option is used for defining the available Message Authentication Code (MAC) algorithms. These are used to protect the integrity of data.
- MaxAuthTries
This option defines the maximum number of times a user can try to authenticate to the server.
- PasswordAuthentication
Defines whether a remote user can log in using password-based authentication.
- PermitEmptyPasswords
This option specifies whether users can use an empty password for remote logins.
- PermitRootLogin
This option defines whether root login is allowed or not.
- PermitTTY
This option defines if pseudo TTY is allowed or not.
Uncomment the line that contains one of the above options and set the desired option value. The below section illustrates some common security hardening practices for OpenSSH.
How to Harden OpenSSH Server Security
Since OpenSSH acts as the front door to your server, it is extremely important to harden its security. Try to maintain the following suggestions to make remote login extra secure.

1. Disable Root Login
You should never permit root login on your ssh server since an escalation of the root account can compromise the entire server. Moreover, the root user account is constantly targeted by malicious users. So, it is better to create a regular user and allow sudo permissions to it. You can Disable root login by setting the value of PermitRootLogin to no.
PermitRootLogin no
2. Limit Authentication Attempts
Admins must limit the number of login attempts from remote hosts to prevent brute-force login attempts. The rising of vast bot armies has made this more important than ever. Use the MaxAuthTries option to set the number of allowed authentication attempts to your server. Many admins consider three to be an acceptable value for this option. However, you can set it based on your security standards.
MaxAuthTries 3
3. Reduce Login Grace Time
Another way to prevent automated bots is to reduce the login grace time. This is the amount of time within which a user must authenticate successfully after connecting to the server. The sshd_config file defines this value in seconds.
LoginGraceTime 20
4. Disable Password Authentication
You should only allow users to log in to the server using key-based authentication. So, make sure to disable the password-based authentication scheme. You can do this by setting the value of PasswordAuthentication to no.
PasswordAuthentication no
It is also a good idea to disable empty passwords. Set the value of the PermitEmptyPasswords field to no.
PermitEmptyPasswords no
5. Disable Other Authentication Methods
OpenSSH supports some additional authentication methods other than key-based and password-based authentication. You should disable them altogether after setting up key-based authentication and disabling password authentication.
ChallengeResponseAuthentication no KerberosAuthentication no GSSAPIAuthentication no
6. Disable X11 Forwarding
X11 forwarding is used to display graphical applications on the server to the remote host machine. However, it is not needed for most enterprise servers. So, disable it if you do not require this feature.
X11Forwarding no
After disabling X11 Forwarding, you need to comment out all references to AcceptEnv. Simply add a hash(#) before the lines to comment on them.
7. Disable Miscellaneous Options
Disable the following options used for tunneling and forwarding if you do not need them for your server.
AllowAgentForwarding no AllowTcpForwarding no PermitTunnel no
8. Disable SSH Banner
The verbose ssh banner is enabled by default and displays essential information about the server. Hackers can leverage this information to plan an attack on your server. So, it is a good idea to disable the verbose ssh banner.
DebianBanner no
If this option is not present in your sshd_config file, add it for disabling the banner.
9. Implement IP Address Allow List
In most cases, you will access the remote server from a handful of known IP addresses. You can create an IP address allow the list to prevent other people from accessing your server. This reduces the risk of a server breach, even if your private keys have become compromised.
However, you should be careful when implementing the IP allow list and refrain from using dynamic addresses since they change very frequently.
To define the allow list, first find out the IP address you are currently using to connect to the OpenSSH server. You can do this by running the following command in your terminal.
$ w
Note the IP address under the label ‘FROM‘. We will assume an example IP address of 203.0.113.1 for the rest of this guide. Now, open your ssh configuration file and use the AllowUsers configuration directive, as shown below.
AllowUsers *@203.0.113.1
The above line will restrict all remote users to a select IP address. You can change this to an IP address range using the Classless Inter-Domain Routing (CIDR) notation, as illustrated below.
AllowUsers *@203.0.113.0/24
10. Restrict the Shell of Remote Users
It is always a good practice to restrict the operations carried out by the remote user. You can do this by restricting the remote user’s shell. OpenSSH allows multiple configuration options to aid in this task. We will show you how to restrict a users’ shell access to SFTP-only using these options.
First, we will create a new user called mary using the /usr/sbin/nologin shell. This will disable interactive logins for that user but still provide non-interactive sessions to carry out operations like file transfers.
$ sudo adduser --shell /usr/sbin/nologin mary
This command creates the user mary with nologin shell. You can also disable the interactive shell for an existing user by using the following command.
$ sudo usermod --shell /usr/sbin/nologin alex
If you try to log in as one of the above users, your request will be rejected.
$ sudo su alex This account is currently not available.
However, you can still perform actions that do not require an interactive shell by using these accounts.
Next, open up your sshd configuration once more and use the ForceCommand internal-sftp and ChrootDirectory directive for creating a highly restrictive SFTP-only user. We are going to restrict the user alex for this example. Also, it is highly recommended to add any Match blocks at the bottom of your sshd_config.
Match User alex ForceCommand internal-sftp ChrootDirectory /home/alex/
Quit the configuration file and test whether the configuration file causes any error or not. You can do this by running the following command in your Linux terminal emulator.
$ sudo sshd -t
If everything goes alright, you should have created a robust configuration for the user alex. The interactive login session is disabled for this user, and he has access to only the home directory of his account.
Ending Thoughts
Since OpenSSH is integral to your remote server’s security, it is essential to learn how it works. That is why our editors have presented various useful information regarding the OpenSSH server in this guide. The topics include how OpenSSH works, how to read and edit the configuration file, and how to implement the best security practices.
Hopefully, we were able to provide the information you were looking for. Bookmark this guide for future references. And do not forget to leave a comment if you have any more queries or suggestions on making this guide more usable.